What is Cybersecurity? Importance and its uses & the growing challenges in 2024!
Sep 27, 2024 4 Min Read 3647 Views
(Last Updated)
Look around today, you will witness that we are more reliant on technology and devices than ever before. Benefits of this trend range from getting rid of Yellowbook, and having near-instant access to information on the internet o the modern conveniences provided by smart home automation technology and concepts like IoT devices.
With so many great things coming from technology, it’s highly likely that some potential threats lurk behind every device & platform. Despite the world’s optimistic perception of modern devices, cyber threats possess an inevitable danger.
Table of contents
- What is Cybersecurity?
- 5 Reasons Why Cybersecurity Is So Important
- Cybercrime is on the Rise.
- Damage is Significant.
- Cybersecurity builds trust.
- Our Identities protect our data
- Every Organization has vulnerabilities.
- What is a Cyberattack?
- Denial of service
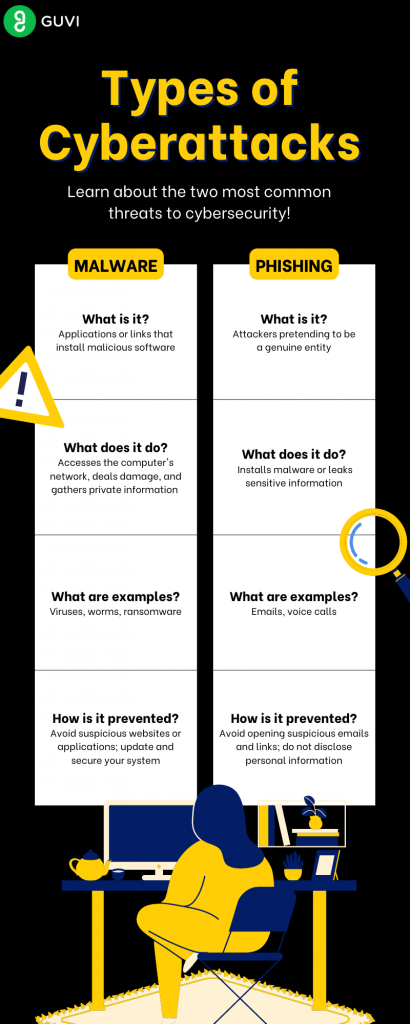
- Malware worms and Trojan horses
- Botnets and Zombies
- Scareware
- Man-in-the-middle
- SQL Injection
- What we can do to curb Cyberattacks?
- Planning
- Implementing
- Reviewing
- What are the growing Cybersecurity Challenges?
- Sheer Volume of Data to safeguard
- Workforce Dependency
- Black Market Tools
- The Weaponization of Social Media
- Security Risks Concerning IoT Devices
- Shortage of Vetted Cyber professionals
- Password Reuse
- Cloud Vulnerabilities
What is Cybersecurity?
With more and more daily business activities moving online, it is becoming increasingly important for companies to ensure that no one is attempting to steal their data or money. According to Cybercrime Magazine, cybercrime will cost the world $10.5 trillion annually by 2025! That’s why cybersecurity plays a significant role in business. Cybersecurity involves the protection of computer-based equipment and information from unintended or unauthorized access change or destruction.
It is a process or state of protecting as well as recovering computer systems, devices, networks, and programs from any form of cyber attacks
5 Reasons Why Cybersecurity Is So Important
Cybersecurity is important to every organization, no matter how big or how small.
1. Cybercrime is on the Rise.
There are roughly 4,000 cyberattacks every day. One reason why the rate of cybercrime continues to increase is that it’s cheap, fast, and highly profitable compared to other types of crime, which is why that’s where cybercriminals are headed.
2. Damage is Significant.
Cybercrime can cost organizations Millions of dollars in damages. But it’s just about financial costs. It can also damage their reputation, and their ability to do business, and sometimes even compromise the health of employees, patients, customers, and others.
3. Cybersecurity builds trust.
Cybersecurity affects trust with customers and employees. When people don’t feel that their information is properly secured and kept private, they begin to lose trust in the brand, the product, and the services.
4. Our Identities protect our data
User Identities now protect billions of points of data. This is the Data that we’re transmitting at work, Data from IoT devices like a coffeemaker or the printers we use, and our personal information, as more of our data is becoming digitized. Securing these identities helps to reduce the risk of cybercrime to organizations, and to individuals alike.
5. Every Organization has vulnerabilities.
As organizations evolve merge and grow over time, their networks and systems naturally get more complicated and things may slip through the cracks. Additionally, end users like you and me can often be the weakest link in an organization’s security, and that requires these organizations to put robust security and compliance protections in place.
We should all care about cyber security, it’s part of all of our jobs because it’s an essential part of every organization and when properly implemented a proper security approach can help us maintain a more secure private, and efficient work environment.
What is a Cyberattack?
A cyber attack takes several forms including theft or unauthorized access to computers laptops tablets or mobile devices, a remote attack on IT systems or websites attacks, or the information held in third-party systems such as cloud devices.
If a cyber attack strikes, it can result in financial losses, increased costs of recovery and replacement, damage to reputation, and damage to other dependent or connected companies.
Six main types of cyber attacks have been identified. These are:
Denial of service
Such an attack successfully prevents the authorized functionality of network systems or applications by exhausting resources. Once your system is attacked in this manner the hackers normally ask for our ransom or fee to regain access to files.
Malware worms and Trojan horses
These attacks are deadly viruses that are spread by emails, instant messaging, malicious websites, and affected non-malicious websites
Botnets and Zombies
A “botnet” short for robot Network is an aggregation of compromised computers that are connected to a central controller. Compromised computers are often referred to as zombies. Botnets which are designed to steal data improve their encryption capabilities and thus become more difficult to detect.
Scareware
More commonly understood as fake security warnings. This type of attack can be particularly profitable for cyber criminals as many users believe the following warnings that tell that – “their system is infected or compromised” and then are tricked into downloading and paying for special software to protect their systems.
Man-in-the-middle
The type of cyber attack includes intercepting conversations or data transmissions between one or multiple people. An example would be using an unsecured Wi-Fi network to intercept the data that the victim transmits from their system to the network.
SQL Injection
SQL is short for Standard Query Language. An SQL injection aims towards performing certain actions on Data in a database and potentially corrupting or stealing it. It also includes inserting malicious code via SQL statements and taking advantage of data-driven vulnerabilities.
What we can do to curb Cyberattacks?
It is very important for companies to protect themselves from the threat of scams, data thefts, and other online vulnerabilities. This can be done by:
Planning
–What information assets are critical to your business?
–What kind of risks can they be exposed to?
–What legal and compliance requirements are your business subject to?
Implementing
–Have you put in place the right security controls to protect your equipment, and information IT system, and outsource IT services?
–Does your staff know what their responsibilities are if you are attacked or something goes wrong?
–How will you deal with it and get back to business?
Reviewing
–Are you reviewing and testing the effectiveness of your controls?
–Are you monitoring and acting on the information you receive from them?
–Do you know what are the latest threats?
By asking and answering these and related questions businesses can better mitigate cyber-attacks and prepare effective cybersecurity measures.
What are the growing Cybersecurity Challenges?
Now that you have an idea of what is cybersecurity, Let’s just suggest that there is a litany of issues & challenges facing our digital ecosystem when it comes to cybersecurity.
Sheer Volume of Data to safeguard
First and foremost is the sheer volume of digital assets that we collect, produce, distribute, share, and manage. Many of those assets have extraordinary value to individuals, governments, and organizations. The sheer volume of intellectual property that we produce, it’s not just valuable to those In corporate, clearly, but also to nation-state actors.
Workforce Dependency
There are so many bad actor attacks and the threat environment that’s out there, the security operation teams at top organizations are always occupied because they’re just continually being subject to attack and ensuring that we’re staying on track with security compliance.
Black Market Tools
The ongoing threat landscape is growing more complex. Threat actors can actually buy attack kits on the black market for pennies on the dollar and do extraordinary damage.
The Weaponization of Social Media
The hackers and bad actors have shifted from wanting that kind of information to sell for identity theft and they’ve shifted to a more nefarious kind of role like the Weaponization of social media in 2016 to rig and manipulate elections.
Security Risks Concerning IoT Devices
Internet of Things devices are great, but they are really pushing the barrier far more toward convenience over security. When the Internet of Things devices are used by individuals who cannot or won’t patch and apply security updates.
In many cases, a lot of the vendors don’t make them available to consumers just because the device is so inexpensive in the first place.
So those devices are on the Internet for convenience purposes and people who want to control their electric lights or have an electronic doorbell probably don’t know that these devices are outside of administrative control and we don’t know what they’re doing on our network. So we can mitigate that risk only to a certain extent, but they can also be leveraged for distributed denial of service attacks.
Shortage of Vetted Cyber professionals
It’s growing increasingly more difficult to hire security professionals to get them properly trained, to retain them in our environment. When you compare the need for really qualified people with the threat landscape, organizations have a very complex task to work with. That’s why companies are constantly looking for proficient network and security professionals who can assess and mitigate threats.
If you wanna get started with Cybersecurity, pick this holistic Cybersecurity and ethical hacking course to get your fundamentals clear.
Password Reuse
Additional security threats for everyone on social media include password reuse, You may choose a really strong password, but if you are reusing it on 10 sites & if it’s breached on one site, Hackers can use it on all the other nine and that’s a huge issue.
Organizations need to uphold security awareness education pieces and have their employees and users understand why they need better passwords to prevent these kinds of attacks.
Cloud Vulnerabilities
From a technical perspective, moving to the cloud has enabled a lot of optimization of resources in almost every sector. On the other hand, if you don’t do it smartly, we’re all gonna suffer some massive breaches at the end of it.
So now you know what is cybersecurity, its challenges, its importance, and various kinds of cyberattacks that need to be mitigated. Learn about the cybersecurity certifications that are prerequisites for profound cybersecurity.
























![10 Best Ethical Hacking Project Ideas [With Source Code] 4 Ethical Hacking Project Ideas](https://www.guvi.in/blog/wp-content/uploads/2024/11/Ethical-Hacking-Project-Ideas.png)






Did you enjoy this article?