
Serializability in DBMS: A Detailed Guide
Feb 19, 2026 8 Min Read 1627 Views
(Last Updated)
Why do some database transactions stay perfectly consistent even as countless operations occur at the same time? This question captures the core idea behind serializability in DBMS. It represents a foundational concept that preserves correctness in concurrent transaction processing. Systems grow more complex as multiple users read and modify data, and serializability offers a structured way to maintain reliability. It provides a framework that treats concurrent transactions as though they were executed one after another in a controlled order.
Read the complete blog to gain a clearer and more practical understanding of serializability and its role in reliable database processing.
Quick Answer: Serializability creates a controlled order for concurrent transactions so the database maintains consistent results. The concept works through locking, timestamps, validation, and graph checks that guide operations safely. The structure supports reliable applications because it prevents conflicts and keeps outcomes predictable under heavy workloads.
- Research shows that many commercial systems use weaker isolation levels than serializable by default, which means numerous data integrity anomalies likely occur daily in large systems if serializability is not enforced.
- Leading systems such as PostgreSQL, Oracle, SQL Server, and MySQL support a SERIALIZABLE isolation level, although each engine handles it through its own internal design.
- Research on modular isolation mechanisms reported a system achieving up to 10.5 million transactions per second on a TATP workload while enforcing serializability.
Table of contents
- What is Serializability in DBMS?
- Types of Serializability
- Top Advantages of Serializability in DBMS
- Strong Data Consistency
- Reliable Concurrent Execution
- Clear Conflict Control
- Increased System Trustworthiness
- Foundation for Advanced Concurrency Techniques
- Techniques for Implementing Serializability in DBMS
- Two-Phase Locking
- Steps to Implement This Technique
- Timestamp Ordering
- Steps to Implement This Technique
- Validation-Based Protocol
- Steps to Implement This Technique
- Graph-Based Protocol
- Steps to Implement This Technique
- Strict Locking
- Steps to Implement This Technique
- Example:
- Methods for Testing Serializability in DBMS
- Conflict Testing
- Precedence Graph Testing
- View Testing
- Timestamp Order Verification
- Top Applications of Serializability in DBMS
- Banking and Financial Transaction Systems
- Inventory, E-Commerce, and Order Management Systems
- Reservation, Scheduling, and Ticketing Platforms
- Challenges and Solutions in Guaranteeing Serializability
- High Lock Contention
- Deadlocks During Concurrency Control
- Overhead from Validation and Checking
- Complex Transaction Dependencies
- Long Running Transactions
- Conclusion
- FAQs
- Is serializability the same as SQL’s Serializable isolation level?
- Does serializability slow down a database?
- Do all applications require serializability?
What is Serializability in DBMS?
Serializability in database management refers to a concurrency control concept. It treats overlapping transactions as though they were executed in a clear and ordered sequence, which creates a stable foundation for consistent outcomes. This approach allows each transaction to act as though it had exclusive access to the database.
This sense of isolation reduces the chance of conflicts among read and write operations. The idea becomes clearer once the final result of a schedule is compared with the result of a valid serial order of transactions, because that comparison shows whether the schedule qualifies as serializable.
Types of Serializability

| Type of Serializability | Core Idea | Key Check |
| Conflict Serializability | The commit sequence follows the same order as the serial schedule | Conflicting operations can be rearranged to match a serial order |
| View Serializability | Preserves how transactions read and write data | Final values and read patterns match a valid serial order |
| Commit Order Serializability | Aligns commit order with serial order | Commit sequence follows the same order as the serial schedule |
| Precedence Graph Serializability | Uses a graph to check transaction dependencies | Serializability holds when the graph has |
Top Advantages of Serializability in DBMS

1. Strong Data Consistency
Serializability supports consistency across DBMS projects because each transaction proceeds as though it runs alone on the database. It creates a predictable environment for read and write operations. This structure protects shared values from unintended changes and maintains accuracy across the system.
2. Reliable Concurrent Execution
A database gains stability when concurrent transactions follow an order that aligns with a valid serial schedule. This alignment reduces irregular outcomes because every operation contributes to a result that remains consistent with established transaction rules. The entire workflow becomes steady under varied workloads.
3. Clear Conflict Control
Conflicts involving shared data items become easier to manage when serializability guides how operations appear in a schedule. The organized structure limits interference among transactions and reduces the chance of inconsistent updates, which contributes to cleaner concurrency handling.
4. Increased System Trustworthiness
Applications depend on databases that produce dependable results, and serializability supports this expectation by maintaining logical accuracy through controlled transaction ordering. Developers and users gain confidence because the system behaves stably and predictably across different scenarios.
5. Foundation for Advanced Concurrency Techniques
Several higher-level concurrency mechanisms function properly because serializability in DBMS sets a clear correctness standard. Transaction schedulers, locking methods, and validation protocols all work more effectively when they adhere to a serializable model that guides their decision-making.
Techniques for Implementing Serializability in DBMS
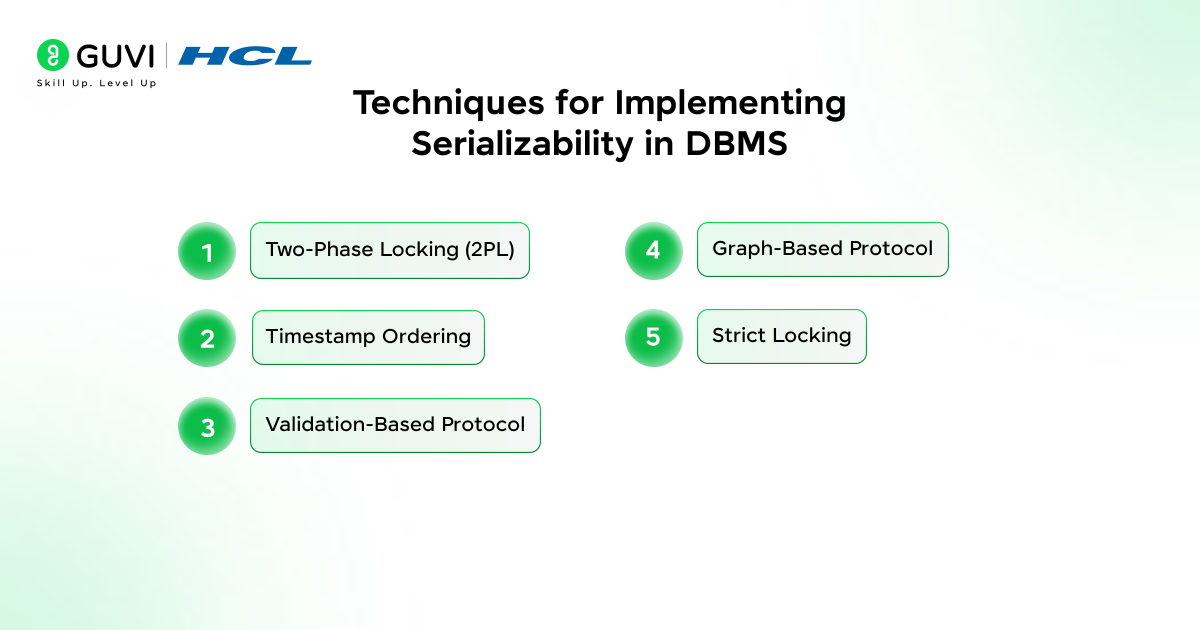
1. Two-Phase Locking
Two-phase locking is a concurrency method that organizes how transactions access shared data so the database produces results that match a valid serial order. The technique creates a clear pattern of controlled access because each transaction gathers locks before performing its work and releases them only after its operations reach completion. This structure supports consistent behavior during concurrent activity and helps the system maintain stable outcomes.
Steps to Implement This Technique
- Lock Acquisition: The transaction collects all required locks on data items before reading or writing them. Each lock request follows established rules that keep access orderly.
- Growing Phase: The transaction continues collecting locks during this phase and avoids releasing any of them. This pattern forms a controlled buildup of access rights.
- Shrinking Phase: The transaction begins releasing locks after it completes its operations. The release pattern follows a clean sequence that prevents interference among active transactions.
- Commit and Cleanup: The system commits the transaction once all locks follow the proper release order. This process helps maintain consistency across concurrent workflows.
Example:
- T1 wants to read X and update Y.
- It takes a shared lock on X and an exclusive lock on Y.
- T2 wants to update X, but it waits because T1 still holds the shared lock on X.
- T1 completes its operations and then releases both locks.
- T2 updates X after the locks are released.
- The overall sequence places T1 before T2, which matches a valid serial order.
Note- T=Transaction
2. Timestamp Ordering
Timestamp Ordering is basically a concurrency method. It organizes transactions based on assigned timestamps so the database follows a clear and consistent order of execution.
Timestamp Ordering places each transaction in a defined position within the schedule. It creates a structured pattern that reduces conflicts among read and write operations. The system uses these timestamps to guide decisions that support stable and correct outcomes across concurrent activity.
Steps to Implement This Technique
- Assign Timestamp: The system provides each transaction with a unique timestamp that represents its position in the global order. This value becomes the reference point for all its operations.
- Check Read and Write Requirements: Each read or write request is compared with timestamps of previous operations on the same data. The comparison helps the system judge whether the request follows the required order.
- Control Conflicting Operations: Operations that appear to violate the timestamp rules are delayed or rejected. The control flow protects the database from producing incorrect results.
- Commit According to Order: The transaction completes only when its operations follow the timestamp sequence. This approach keeps the outcome aligned with a valid serial order.
Example:
- T1 receives timestamp 4, and T2 receives timestamp 10.
- T1 writes value A at its timestamp.
- T2 attempts to write A late timer, and the system checks both timestamps.
- The write from T2 follows the required timestamp order, so it is allowed.
- The schedule behaves as if T1 happens first and T2 happens after, which matches a safe serial order.
Also, Read: 30 Important Database Management Interview Questions and Answers
3. Validation-Based Protocol
Validation-Based Protocol is a concurrency approach that allows transactions to work on local copies of data while delaying conflict checks until they reach the validation stage. The technique creates a controlled pattern where transactions perform their tasks independently and rely on a verification step to confirm that their actions align with a serial order.
This structure supports consistency because the system checks for possible conflicts before committing any changes. It further helps maintain stable outcomes during concurrent processing.
Steps to Implement This Technique
- Perform Local Processing: The transaction completes its read and write actions on local data without affecting other active transactions. This setup reduces direct interference during the early stages.
- Enter Validation Stage: The transaction moves into a verification phase before it commits. The system examines its read and write sets to judge whether conflicts may appear.
- Check for Conflicts: The system compares the transaction’s data sets with those of other transactions that have committed or are in progress. The comparison helps confirm that the order remains consistent.
- Commit After Successful Validation: The transaction takes place only when the validation process shows that its actions align with a correct serial order. This final step maintains dependable results across the database.
Example:
- T3 reads B and C and performs calculations on local copies.
- T4 works during the same time and writes a new value to C.
- T3 enters validation, and the system checks whether T4’s changes affect T3’s work.
- The comparison shows no conflict between their read and write sets.
- T3 commits, and the final result aligns with a correct serial order.
4. Graph-Based Protocol
Graph-Based Protocol is a concurrency technique that organizes transaction relationships through a directed graph so the system can observe how operations depend on one another. The structure creates a clear view of ordering requirements because each edge represents a dependency that forms during read and write actions.
The technique examines this graph to confirm that the schedule remains free of cycles, which supports a serializable outcome and keeps concurrent activity predictable.
Steps to Implement This Technique
- Create Transaction Nodes: The system represents each active transaction as a node in the graph. This layout forms the base structure for recording dependencies.
- Add Directed Edges: The system adds edges between nodes when one transaction must appear before another based on their read or write actions. These edges reflect ordering requirements that guide the schedule.
- Check for Cycles: The graph is examined for the presence of cycles. A cycle indicates that the ordering creates a conflict, which prevents the schedule from being serializable.
- Proceed Only with an Acyclic Graph: The system allows the schedule to continue once it confirms that no cycles exist. This outcome supports correct ordering and maintains consistent results across concurrent operations.
Example:
- T5 writes D.
- T6 reads D afterward, so the system adds an edge from T5 to T6.
- T6 writes E.
- T5 reads E later, which adds an edge from T6 to T5.
- The edges form a cycle between T5 and T6, which shows the schedule cannot be serializable.
- The system stops the conflicting sequence so the schedule stays correct.
5. Strict Locking
Strict Locking is a concurrency method that keeps write locks in place until a transaction commits. It creates a controlled environment where other transactions avoid reading or writing data that may still change.
The approach reduces the chance of inconsistent states because locked items remain stable until the system completes the transaction. This system supports dependable outcomes during concurrent activity. It also helps protect the database from issues that appear when updates are released too early.
Steps to Implement This Technique
- Apply Write Locks: The system places write locks on data items before any updates occur. These locks restrict access, so other transactions wait for a clear and safe point to proceed.
- Hold Locks Until Commit: The transaction keeps its write locks until it reaches the commit stage. This pattern prevents other transactions from reading values that may not be final.
- Queue Conflicting Requests: The system places conflicting read and write requests in a waiting state. This control mechanism keeps operations orderly and reduces unwanted interference.
- Release Locks After Completion: The system releases the locks only after the commit. This step preserves consistency and supports a stable result across concurrent transactions.
Example:
- T7 writes value F and holds an exclusive lock on F until it commits.
- T8 wants to read F but waits because T7 has not committed yet.
- T7 commits and releases the lock.
- T8 reads the final committed value of F.
- This pattern prevents inconsistent reads and protects serializable behavior.
Methods for Testing Serializability in DBMS

1. Conflict Testing
Conflict testing checks whether a schedule can be rearranged into a serial order by swapping operations that do not interfere with one another. The method examines read and write actions that target the same data item and studies how they influence the sequence. A schedule qualifies as conflict serializable when this rearrangement leads to the same outcome as a correct serial order.
How This Method Works:
- Identify Conflicting Actions: The system reviews read and write operations that affect the same data item.
- Examine Order of Conflicts: The sequence of these actions is compared with possible serial orders.
- Rearrange Non-Conflicting Actions: Safe swaps are applied to achieve a cleaner ordering.
- Check the Final Arrangement: The schedule is accepted when the rearranged form matches a serial sequence.
2. Precedence Graph Testing
Precedence graph testing uses a directed graph to study relationships among transactions. Each edge reflects a dependency created by read or write operations. A schedule remains serializable when the graph does not form any cycle.
How This Method Works:
- Create Transaction Nodes: Each transaction becomes a node within the graph.
- Add Dependency Edges: Edges appear when one transaction must occur before another due to data access.
- Inspect the Graph for Cycles: A cycle signals an incorrect sequence.
- Accept Acyclic Graphs: A cycle-free graph represents a valid serializable schedule.
3. View Testing
View testing checks whether a schedule produces the same final values and read patterns as a valid serial order. The method studies how transactions read data and which transaction performs the final write.
How This Method Works:
- Observe Read Patterns: Each transaction’s reads are compared with reads in a serial schedule.
- Review Final Writes: The last write on each data item is matched with the serial version.
- Confirm Matching Effects: The overall behavior is checked for consistency with the serial outcome.
- Accept Only Matching Views: The schedule passes when both reads and final values align with the serial arrangement.
4. Timestamp Order Verification
Timestamp order verification checks whether a schedule follows the required timestamp sequence. Each transaction receives a timestamp that defines its position in the overall order.
How This Method Works:
- Assign Timestamps to Transactions: Each transaction receives a unique starting timestamp.
- Compare Operation Timing: Reads and writes must respect timestamps of earlier actions.
- Detect Any Violations: A violation signals a conflict with the required sequence.
- Accept Schedules That Follow the Order: The schedule qualifies when all operations remain consistent with the timestamp pattern.
Deepen your understanding of database management, data consistency, and concurrency control with our Data Science Course, an industry-ready program co-certified by IITM Pravartak. Learn how data systems maintain reliability through principles like serializability, transaction management, and data validation, while mastering practical tools such as SQL, Python, Power BI, and Machine Learning frameworks. This hands-on, mentor-led course equips you with real-world project experience, personalized placement support, and a globally recognized certification, helping you build a high-impact career in data engineering, analytics, and AI-driven problem-solving.
Top Applications of Serializability in DBMS

1. Banking and Financial Transaction Systems
Serializability plays a vital role in digital banking platforms and core financial engines because it maintains accurate results during concurrent deposits, withdrawals, and balance checks. The model protects account data from inconsistent updates and supports regulatory requirements for transaction correctness in high-volume financial workflows.
2. Inventory, E-Commerce, and Order Management Systems
Large e-commerce and marketing platforms and warehouse management tools depend on serializable behavior to maintain correct stock levels when thousands of users update carts, place orders, or modify product quantities at the same time. The controlled transaction order prevents overselling, inaccurate stock counts, and conflicting updates that can affect customer experience.
3. Reservation, Scheduling, and Ticketing Platforms
Airline booking engines, hotel reservation systems, transportation schedulers, and event ticketing platforms rely on serializability. This reliance helps avoid double bookings and maintain accurate availability. The predictable transaction flow supports real-time seat allocation and slot management across heavy and concurrent user activity.
Challenges and Solutions in Guaranteeing Serializability

1. High Lock Contention
Problem: Several transactions often compete for the same data items, which creates long waiting times and slows the system during peak activity. The delays reduce throughput and make the system feel less responsive.
Solution: The database can use finer-grained locks and careful scheduling to reduce the number of transactions waiting for access. This approach creates a smoother flow of operations because it spreads contention across smaller parts of the data.
2. Deadlocks During Concurrency Control
Problem: Transactions sometimes wait on each other in a circular pattern, which stops progress entirely. The system remains stuck because each transaction holds a lock that another transaction needs.
Solution: Deadlock detection and timeout mechanisms interrupt these cycles. The system identifies the problematic group and rolls back one transaction, which clears the path for others to proceed.
3. Overhead from Validation and Checking
Problem: Validation methods create processing overhead because the system must compare active transactions with those that have committed. Heavy workloads increase this cost and reduce performance.
Solution: Efficient indexing and optimized validation checks reduce the time required to compare read and write sets. The system completes the checking process more quickly and maintains consistency.
4. Complex Transaction Dependencies
Problem: Complicated dependencies among transactions make it difficult to confirm whether a schedule remains serializable, especially when several data items interact at the same time.
Solution: Precedence graphs and structured dependency tracking simplify this evaluation. The system identifies risky patterns early and prevents schedules that may produce incorrect results.
5. Long Running Transactions
Problem: A transaction that takes too long holds resources for an extended period, which blocks other transactions and increases the chance of conflicts.
Solution: Breaking long transactions into controlled segments reduces blocking and helps the system manage concurrency more efficiently. Each segment completes sooner, which improves the overall flow.
Conclusion
Serializability plays a central role in building reliable database security systems because it guides concurrent transactions toward outcomes that match a correct and predictable order. The concept supports consistency, reduces conflicts, and strengthens the accuracy of results across varied workloads. A clear understanding of its types, techniques, testing methods, and challenges helps teams design systems that behave in a steady and trustworthy way. This knowledge prepares developers to manage complex concurrency with confidence.
FAQs
1. Is serializability the same as SQL’s Serializable isolation level?
Serializability is a theoretical correctness model, while a Serializable isolation level is a practical implementation provided by a DBMS. Some systems implement it through strict checks, and others approximate it through methods like predicate locking or validation.
2. Does serializability slow down a database?
Serializability can add overhead because it controls how transactions interact, especially under heavy workloads. Modern systems reduce this cost with optimized locking, improved timestamp methods, and multi-version concurrency control.
3. Do all applications require serializability?
Many workloads benefit from it, especially financial, inventory, and booking systems where accuracy matters. Other applications choose weaker isolation levels when performance is more important than strict consistency.
































Did you enjoy this article?