Hashing in Data Structure: Definition, Working, and Types Explained (2025)
Nov 26, 2025 5 Min Read 2715 Views
(Last Updated)
When you start learning data structure, concepts like arrays, stacks, and linked lists come first. But when you learn more, you come across the term that takes data and storage to a whole different level: Hashing in data structures. Hashing is helpful for a programmer to hold data and retrieve it almost instantly. It uses a method of transforming each individual item of data into a unique number. Hashing may seem intimidating now, but once you are familiar with it, you will see its elegance, simplicity, and ability!
In this blog, you will learn about hashing in data structures, why it is important, how it works, and the real-world applications of hashing.
Table of contents
- What is a Hash Function?
- Why is Hashing Important in Data Structures?
- Key Terms in Hashing
- How Hashing Works (Step-by-Step)
- What is a Hash Function?
- Properties of a Good Hash Function
- Examples of Simple Hash Functions
- What is a Hash Table?
- Collision in Hashing
- Collision Handling Techniques
- Open Addressing
- Separate Chaining
- Load Factor and Rehashing
- Applications of Hashing in Data Structures
- Wrapping it Up…
- What is hashing in a data structure?
- What is a hash function?
- What is a collision in hashing?
- How are collisions handled?
- What is the load factor?
What is a Hash Function?
Hashing in Data Structure is a procedure of assigning data (also referred to as keys) to a particular position in a data table based on a mathematical algorithm referred to as a hash function.
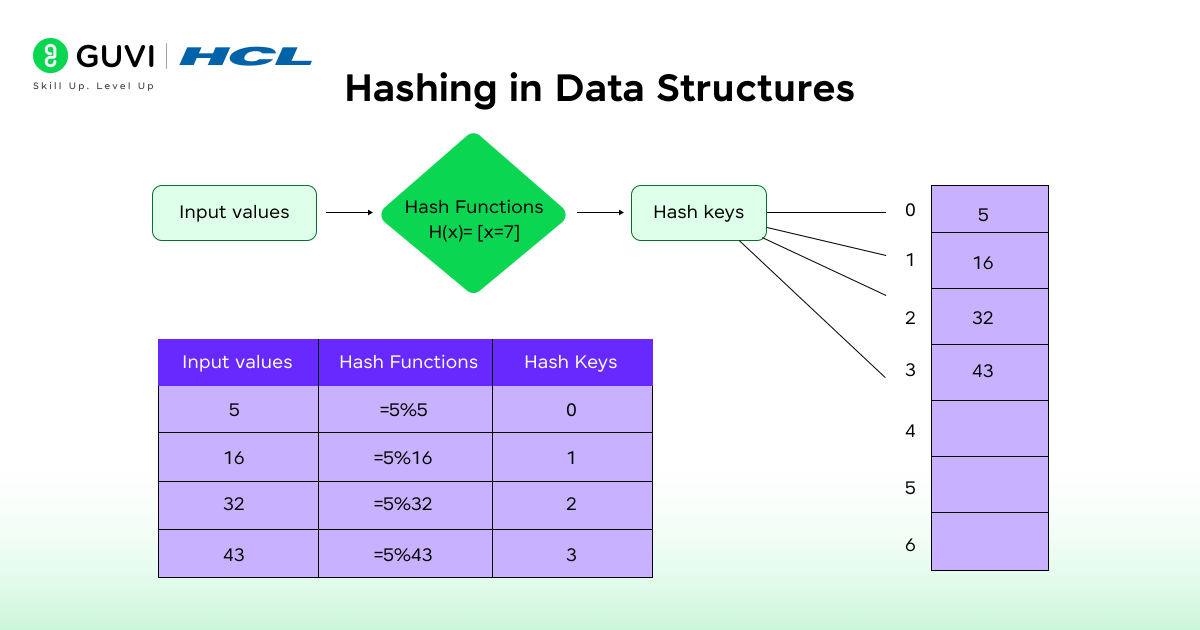
In simple terms:
- All the keys (such as name, ID, or number) are inputted in a hash function.
- The hash algorithm transforms it into a hash code (unique number).
- This hash value then defines the place where the information is stored in a table known as a hash table
So that the hash function will find that data practically in a moment when you need it, without having to search the whole set of data.
Why is Hashing Important in Data Structures?
If there is no hashing, the retrieval of data can be very difficult.
For example:
- You may be required to search an element in arrays or linked lists at a time, which is an O(n) operation.
- In binary search trees, the complexity is lowered to O(log n), but still, that is not immediate.
Hashing, however, can usually provide O(1) average time complexity; that is, the access time does not increase with the amount of data.
That’s why hashing forms the foundation for many efficient data structures, like:
- Hash tables
- Hash maps
- Sets
- Dictionaries
Key Terms in Hashing
It is important to know some key terminologies in hashing before going any further:
| Term | Description |
| Key | The unique input value (like an ID or name) used to identify data. |
| Hash Function | A function that converts a key into a hash code or index. |
| Hash Table | A data structure that stores key-value pairs based on hash codes. |
| Hash Code / Hash Value | The numeric value generated by the hash function. |
| Collision | When two keys map to the same hash value. |
| Load Factor | The ratio of stored elements to the size of the hash table. It helps decide when to resize or rehash. |
- The concept of hashing dates back to the 1950s long before modern computers became mainstream.
- Hash functions play a critical role in cryptography your passwords are stored as hashes, not plain text!
- Popular programming languages like Python, Java, and C++ use hashing to manage data structures such as dictionaries, maps, and sets.
- A well-designed hash function can make data retrieval up to 100x faster than a linear search.
- Even a tiny input change like turning “data” into “Data” produces a completely different hash value!
How Hashing Works (Step-by-Step)
Let’s see how hashing works with a simple example
Assume you would like to save student IDs:
Student IDs: 101, 102, 103, 104, 105
Hash function: h(key) = key % 10
Now apply the hash function:
h(101) = 1
h(102) = 2
h(103) = 3
h(104) = 4
h(105) = 5
The hash table will appear as follows:
| Index | Data |
| 0 | — |
| 1 | 101 |
| 2 | 102 |
| 3 | 103 |
| 4 | 104 |
| 5 | 105 |
The hash function simply refers to index 3 when you need to access the ID 103. No searching at all!
What is a Hash Function?
Hashing is based on a hash function. It transforms a specified key into a smaller size fixed number, also known as a hash value or index, to store and access data.
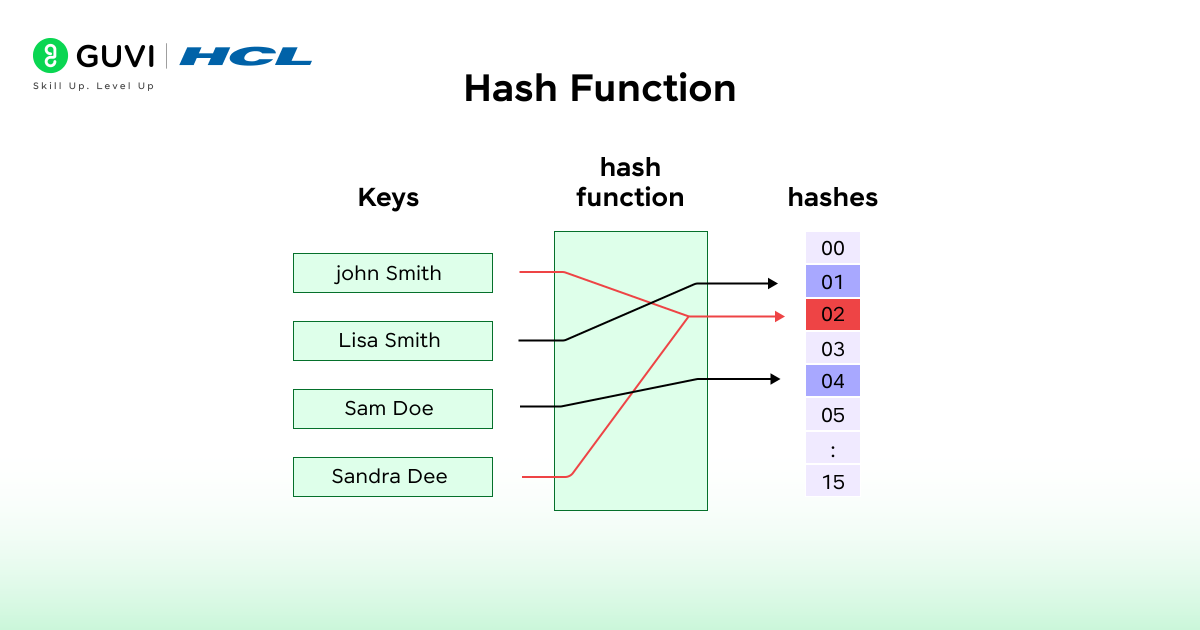
Properties of a Good Hash Function
- Reduces collisions: Different keys should ideally produce different hash values.
- Even distribution: The data is expected to be evenly distributed over the hash table.
- Quick calculation: Must be able to calculate hash values fast.
- Deterministic: The same input must generate the same hash.
Examples of Simple Hash Functions
- Division Method:
- h(key) = key % tablesize
- Multiplication Method:
- h(key) = floor(tablesize (key A % 1))
- where A is a constant that is in the range of 0 to 1.
- Mid-Square Method:
- Square the key and extract some middle digits.
Also Explore: 5 Best Reasons to Learn Data Structures and Algorithms [DSA]
What is a Hash Table?
A hash table is a data structure in which key-value pairs are stored in hashing.
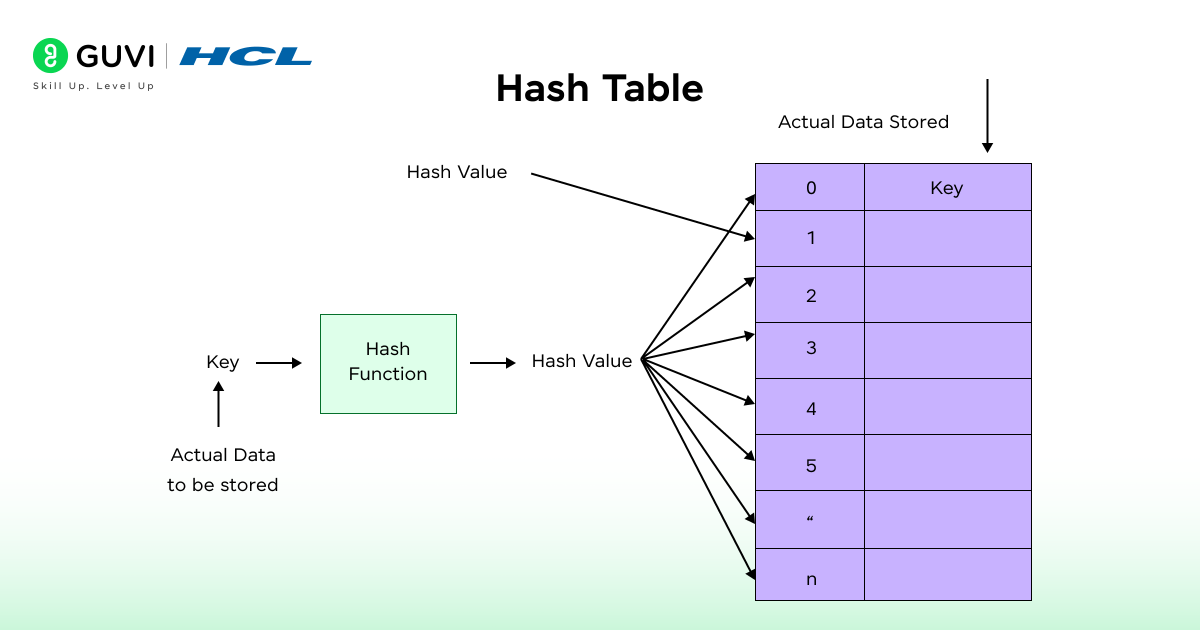
It contains:
- An array of slots (buckets)
- Each bucket stores data at the index produced by the hash function.
For Example:
Let’s store employee names using their employee IDs as a key.
| ID (Key) | Name (Value) |
| 1 | Visha |
| 2 | Priya |
| 3 | Meera |
The hash function maps each key to a table index, allowing quick access.
Download HCL GUVI’s free Data Structures & Algorithms eBook and start mastering problem-solving skills that every top developer needs!
Collision in Hashing
A collision happens when two different keys are mapped to the same index in a hash table by the hash function.
For example, if we use the hash function h(key) = key % 10 and have keys 101 and 111, both will produce the same index 1.
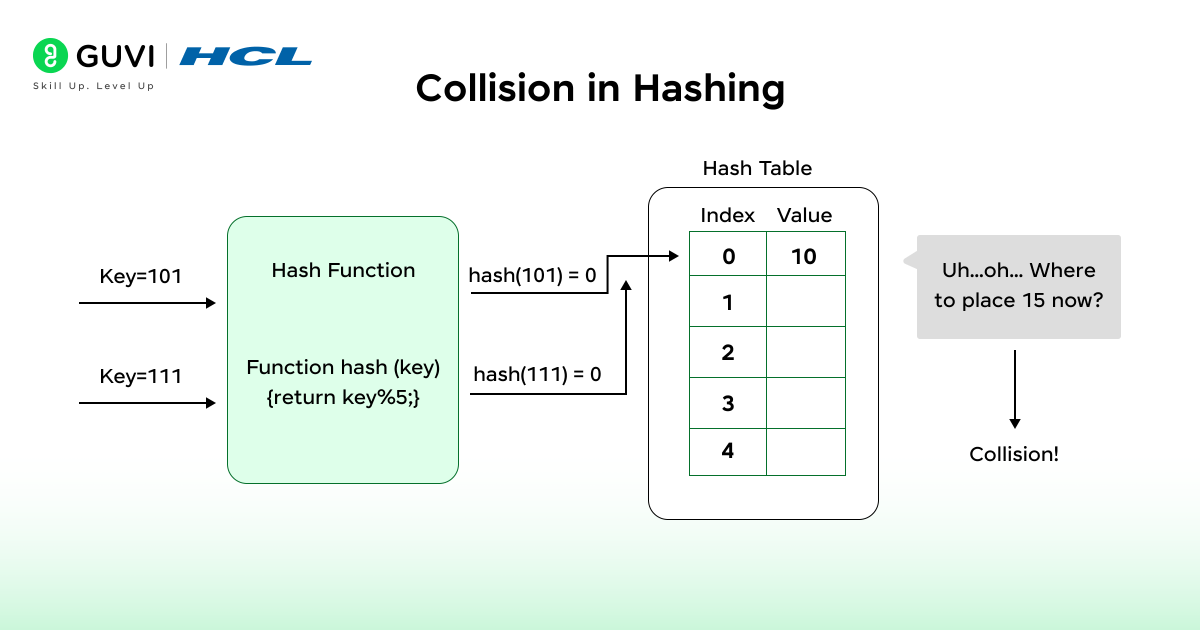
Since the table can’t store both at the same position, this creates a collision. Collisions are inevitable because the number of possible keys usually exceeds the number of available slots.
If collisions are not handled correctly, they may lead to data being overwritten or you may get an access error for the data. For this reason, all hashing strategies have a way to account for and handle collisions.
The two most common collision-handling strategies are the following:
- Open Addressing: All elements are kept in the hash table itself.
- Separate Chaining: Each index in the hash table maintains a linked list of keys that contain the same hash value.
Also Read: Is DSA Important for Placement in 2025?
Collision Handling Techniques
1. Open Addressing
In Open Addressing, every item is kept directly in the hash table itself. If there is a collision, the algorithm will find the next available slot in a predetermined sequence. No auxiliary data structure (like a linked list) is used for storing items. Everything is kept inside the table.
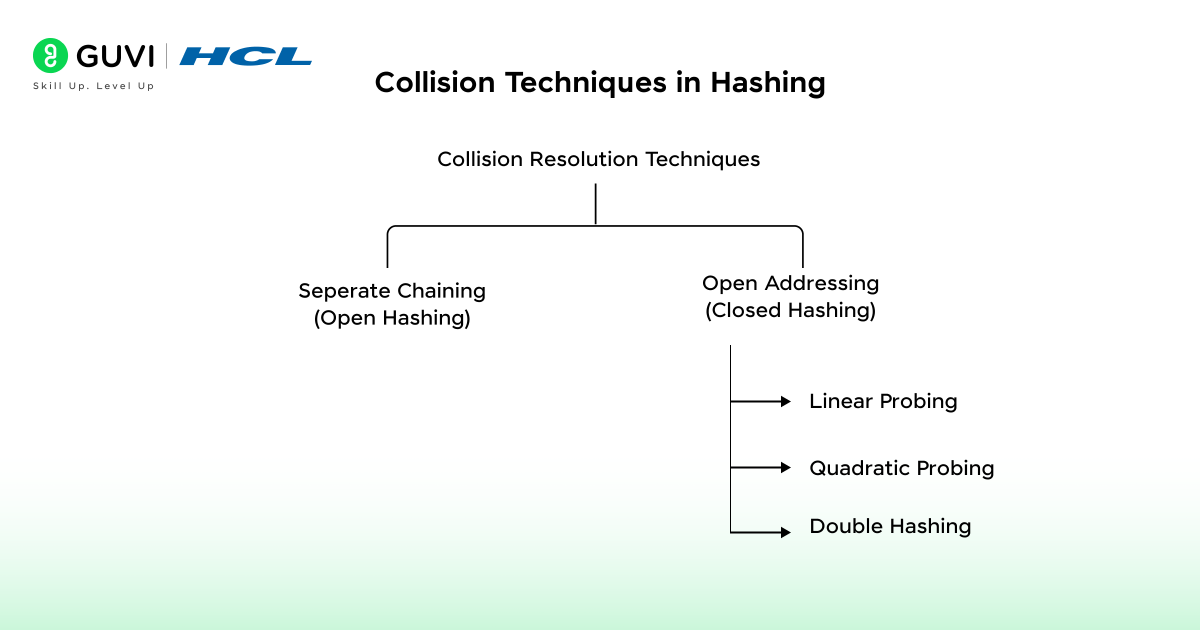
There are three types of open addressing:
- Linear Probing:
In this method, if there is a collision, the algorithm looks at the next slot in the sequence and checks that slot to see whether it is empty.
- Formula: index = (hash + i) % table_size
- Disadvantage: it can create clustering, which is where several keys end up being grouped together. This can lessen the performance of a search.
- Quadratic Probing:
This function jumps in increasing squares instead of moving just one slot at a time (1, 4, 9, etc.).
- Formula: index = (hash + i²) % table_size
- Advantage: quadratic probing creates less clustering than linear probing, and thus generally increases the speed of lookups.
- Double Hashing:
When a collision happens, the algorithm performs another hash value (from the hash value) to calculate how far to move next.
- Formula: index = (h1(key) + i*h2(key)) % table_size
- Advantage: this form reduces both primary and secondary clustering, which makes it the quickest of the three hashing types.
Also Read: Best DSA Roadmap Beginners Should Know 2025
2. Separate Chaining
In the Separate Chaining approach, each slot in the hash table contains a linked list (or sometimes a different data structure, such as a dynamic array) that holds all the elements that share the same hash index. Instead of checking for another empty slot in the table, the collided elements are simply added to the same chain.
For example:
If both keys 101 and 111 hash to index 1, they are stored as follows:
Index 1 → [101 → 111]
Advantages:
- Simple and easy to understand and implement.
- Unlike linear probing, the hash table does not need to be resized often because the chains can grow dynamically.
Disadvantages:
- The downside is that it does require additional memory for the linked lists.
- In the worst case (when many elements collide to the same index) the search time can degrade to O(n) rather than O(1).
Load Factor and Rehashing
The load factor (λ) of a hash table quantifies the fullness of the table. The load factor is calculated as shown below:
Load Factor (λ) = Number of elements stored/Table size
A low load factor indicates that there will be a high number of empty slots in the hash table and resulting in lower collisions, while higher load factors will result in more collisions and increased slowness.
To keep efficiency + performance well and relatively low, many hashing utility libraries will set the load factor threshold to 0.7 (70% full). When the load factor threshold has been hit or exceeded, rehashing will be conducted.
Rehashing means the library will create a new hash table that is larger than the old one by usually twice 2 size of the old hash table’ size and will insert the current hash table elements into the new hash table. This would ensure all elements are hashed anew through the past or newer improved hash function and allows for better distribution of the data, reduced number of collisions, and keeps the average performance time complexity of all three operations (inserting, deletion, search) at nearly O(1) from its past state while growing and size of the data in the dataset.
Also, Explore About 10 Best Data Structures and Algorithms Courses [2025]
Applications of Hashing in Data Structures
- Databases: databases utilize indexing, which is a method of fast data retrieval based on hashing.
- Password management software: Systems store passwords as hash codes for security.
- Compilers: Compilers use a technique called hash tables as an effective way to store a symbol table that contains names of previously defined variables and function names.
- Caches: Lookups of caches are accomplished through hash maps.
- Blockchain: Blockchain systems use cryptographic hash functions as a means to ensure data integrity.
- File systems: File systems use hashes as a means to efficiently traverse files in a folder or an organization system, as well as to identify duplicates.
- Search engines: URL hashing is use to quickly retrieve a previously indexed web page quickly and efficiently.
If you found hashing fascinating, it’s time to take your DSA learning to the next level. Join HCL GUVI’s AI Software Development, co-created with IIT-M Pravartak, and master concepts like hashing, sorting, trees, and graphs with real-world projects and expert mentors.
Wrapping it Up…
Hashing in Data structures is the key to fast data access, rapid searching, and efficient memory usage in today’s computing.
From storing passwords securely to performing fast database queries, hashing is present in almost every digital system you use. Studying hashing may help you design better algorithms, provide ideas for improving code performance, and certainly augment your foundations in computer science.
So next time you are thinking of searching through data, think of hashing, because now you don’t have to search!
Hope this blog made the concept of Hashing in Data structures simple, clear, and practical for your learning journey. Happy learning!
1. What is hashing in a data structure?
Hashing is a technique to map data into a fixed-size table using of a hash function to find, insert, and delete data quickly.
2. What is a hash function?
A hash function will take an input (key) and convert it into a hash value which is used as an index to store the data in a hash table.
3. What is a collision in hashing?
A collision occurs when two different keys have the same hash value or index.
4. How are collisions handled?
Collisions are handled through chaining, open addressing, linear probing, or double hashing.
5. What is the load factor?
A load factor is a measure of how full the hash table is, and when the load factor exceeds a certain amount, rehashing typically occurs to improve efficiency.























Did you enjoy this article?