
What is Agent-to-Agent (A2A) Protocol in Artificial Intelligence?
Oct 07, 2025 6 Min Read 831 Views
(Last Updated)
With AI adoption projected to contribute $15.7 trillion to the global economy by 2030 (PwC), the question is no longer about single models but about how autonomous agents coordinate and deliver results at scale. This is where the Agent-to-Agent (A2A) protocol becomes central. They provide the structured rules that allow machines to exchange information and perform tasks securely.
In this blog, you will explore its architecture, benefits, industry use cases, and the future of A2A. Keep reading to understand why this protocol is shaping the next era of AI-driven ecosystems.
Table of contents
- What is A2A Protocol in AI?
- Core Architectural Components of the A2A Protocol
- Top Benefits of the A2A Protocol
- A2A Protocol in Middleware
- How does the A2A Protocol work?
- Industrial Use Cases of the A2A Protocol
- Difference Between MCP and A2A
- Future of the Agent-to-Agent (A2A) Protocol in AI
- Conclusion
- FAQs
- How does the A2A protocol improve multi-agent collaboration?
- Why is security central to A2A protocol design?
- What role do agent cards play in A2A ecosystems?
- How is A2A applied in cloud and distributed AI systems?
- What makes A2A different from traditional enterprise communication protocols?
What is A2A Protocol in AI?

Agent-to-Agent (A2A) protocol in AI refers to a communication and coordination protocol between autonomous AI agents. This protocol helps share tasks and collaborate (or sometimes compete) without direct human intervention. A2A protocol is completely different from traditional client-server or application-to-application (A2A) interactions in enterprise systems. This protocol in AI emphasizes autonomous decision-making. It is the torchbearer of adaptive behavior and emergent coordination within multi-agent environments.
A2A involves defining interaction languages and protocols such as: FIPA ACL, KQML, or custom message-passing formats) at a technical level. They support semantics like requests, commitments, queries, negotiations, and informative updates. Agents may use natural language or structured symbolic messages. They also employ embeddings for efficient communication. This usage is mainly dependent on the environment.
Core Architectural Components of the A2A Protocol
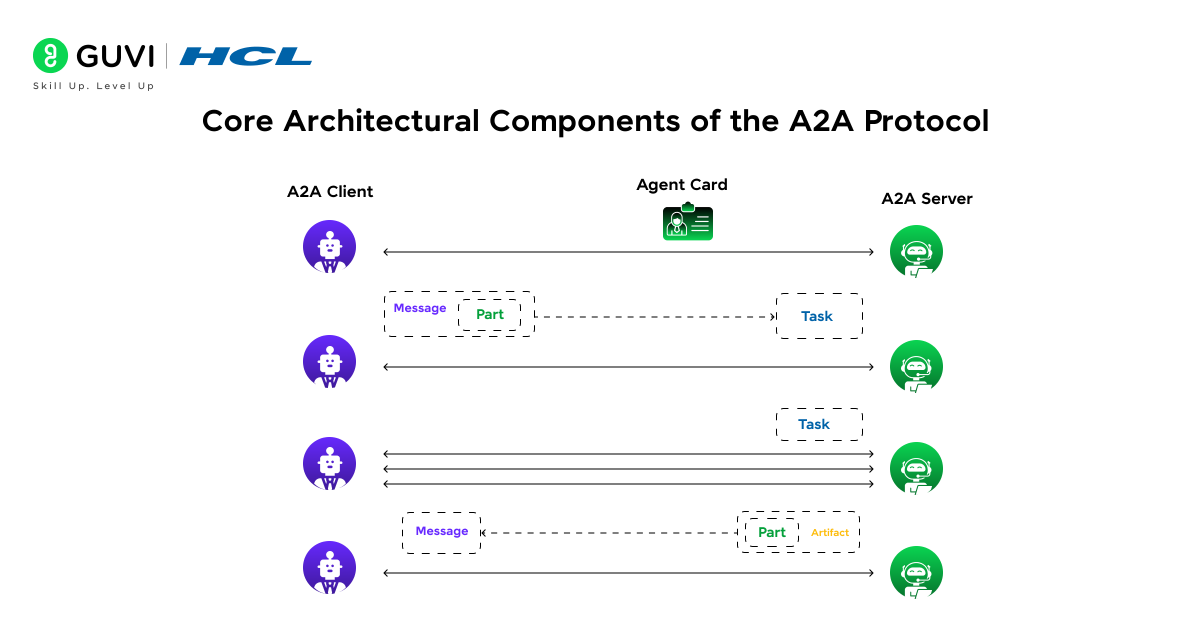
The Agent-to-Agent (A2A) protocol relies on defined components that create order and predictability in agent interactions. Each component fulfills a distinct purpose and connects with others to establish a complete framework.
- A2A Client (Client Agent)
The client agent initiates the interaction workflow. It sends requests to the remote agent and expects responses or outcomes in return. The client agent handles discovery queries and prepares authentication credentials. The client then formats initial tasks into standardized requests. This role mirrors the initiator of communication in the client-server model and sets the sequence of exchanges in motion.
- A2A Server (Remote Agent)
The remote agent acts as the server that responds to client requests. It receives tasks and validates the authenticity of the requesting agent. It also performs the necessary operations. The remote agent can provide services or share data. It can also coordinate actions with the client agent. Its responses must comply with the agreed protocol specifications to maintain consistency.
Also, Read: Agents in Artificial Intelligence: Working, Architecture & Classification
- Agent Card
An agent card contains descriptive metadata about an agent. It typically includes identifiers, capabilities, supported tasks, authentication methods, and service endpoints. The card functions like a digital identity document that allows agents to understand what services are available and under what rules they can be accessed. This component supports both discovery and negotiation phases of the protocol.
- Task
A task represents the unit of work that one agent requests another to perform. Tasks are expressed in structured formats and can vary in complexity from a simple query to a multi-step operation. The task description defines objectives and expected outputs. This clarity allows the receiving agent to allocate resources and respond effectively.
- Message
A message is the communication envelope that transports tasks and status updates between agents. It includes headers and cryptographic signatures that guarantee authenticity and integrity. Messages form the backbone of the A2A workflow because every request and acknowledgment depends on them.
- Artifact
An artifact is the tangible outcome of a completed task. It can be a dataset, a generated report, a trained model, or any digital product that results from agent activity. Artifacts are often accompanied by metadata that validates their origin and links them back to the initial task request.
- Part
A part is a modular element within an artifact or message. Parts allow agents to handle information at a granular level and to compose larger structures from smaller verified elements. This modularity helps in complex workflows where different agents contribute specific parts that together complete a broader objective.
Top Benefits of the A2A Protocol
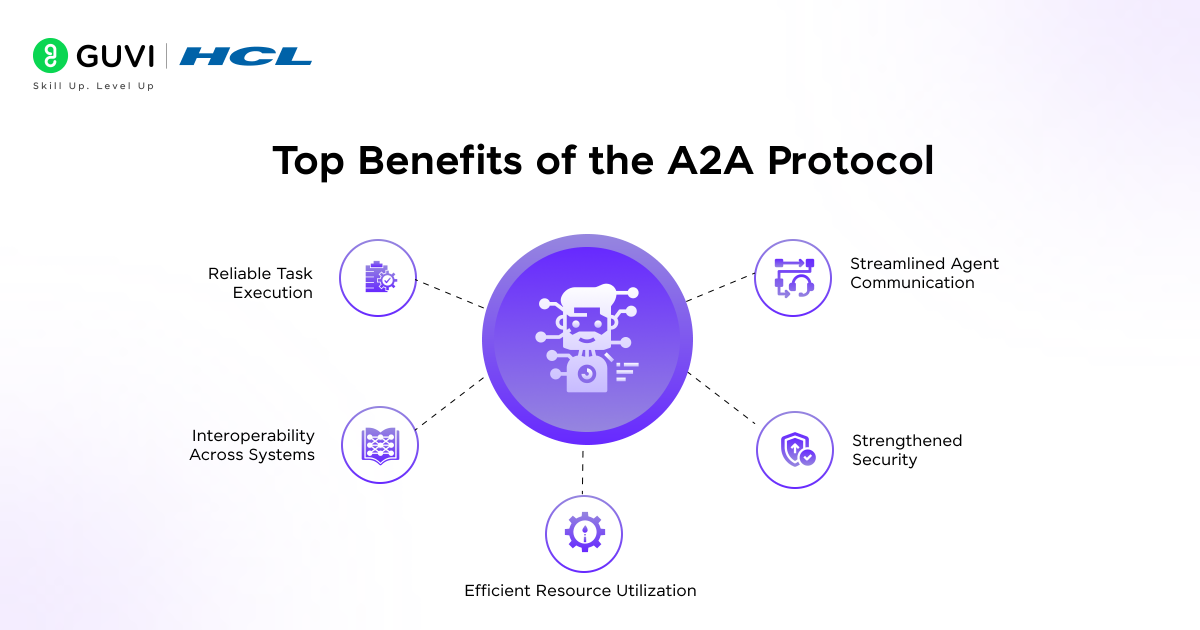
- Streamlined Agent Communication
The protocol standardizes how agents exchange information. Clear message structures and well-defined semantics reduce misinterpretation. Agents can interact with precision, which lowers coordination overhead.
- Strengthened Security
Authentication and cryptographic validation protect agents from impersonation and unauthorized access. The protocol enforces verification at each interaction stage. This guards systems against malicious actors and strengthens trust across agents.
- Reliable Task Execution
Defined workflows help agents execute tasks consistently. The use of artifacts and parts allows outputs to be validated and traced back to the original request. This reliability supports accountability and reproducibility.
- Interoperability Across Systems
Agent cards and standardized messaging formats allow different agents to interact regardless of their underlying architecture. Interoperability supports diverse applications such as robotics, finance, or distributed AI ecosystems.
- Efficient Resource Utilization
Discovery and structured negotiation prevent wasted effort by aligning agents before tasks are initiated. Resources are allocated only to authenticated and valid interactions. This efficiency improves overall system performance.
Find out how multi-agent ecosystems are shaping the future of AI and prepare yourself with our Artificial Intelligence and Machine Learning Course, certified by Intel. This industry-recognized course empowers you to master core AI skills, build intelligent models, and gain hands-on experience with real-world projects. Start your AI journey today and get the Intel-certified edge that employers trust.
A2A Protocol in Middleware
Middleware has always served as the connective tissue in distributed computing, bridging applications, databases, and services. The A2A protocol strengthens middleware by providing standardized mechanisms for autonomous agent interactions. In this context, middleware becomes more than a passive message bus. It transforms into an intelligent coordination layer where agents exchange requests and collaborate on tasks securely.
Traditional middleware solutions often regulate simple routing and message delivery. Middleware can support advanced features such as semantic messaging and artifact exchange with A2A embedded. An A2A-enabled middleware platform allows agents to not only pass data but also negotiate resource allocation and generate validated outputs. This adds value in scenarios where multiple independent agents must interact across heterogeneous environments.
Use cases include microservices architectures where middleware integrates A2A communication between containerized services and hybrid cloud platforms where distributed agents must maintain consistent workflows. Middleware evolves into a foundation for scalable and autonomous AI-driven infrastructures by incorporating the A2A protocol.
How does the A2A Protocol work?

Let us understand the three-step working mechanism.
- Discovery
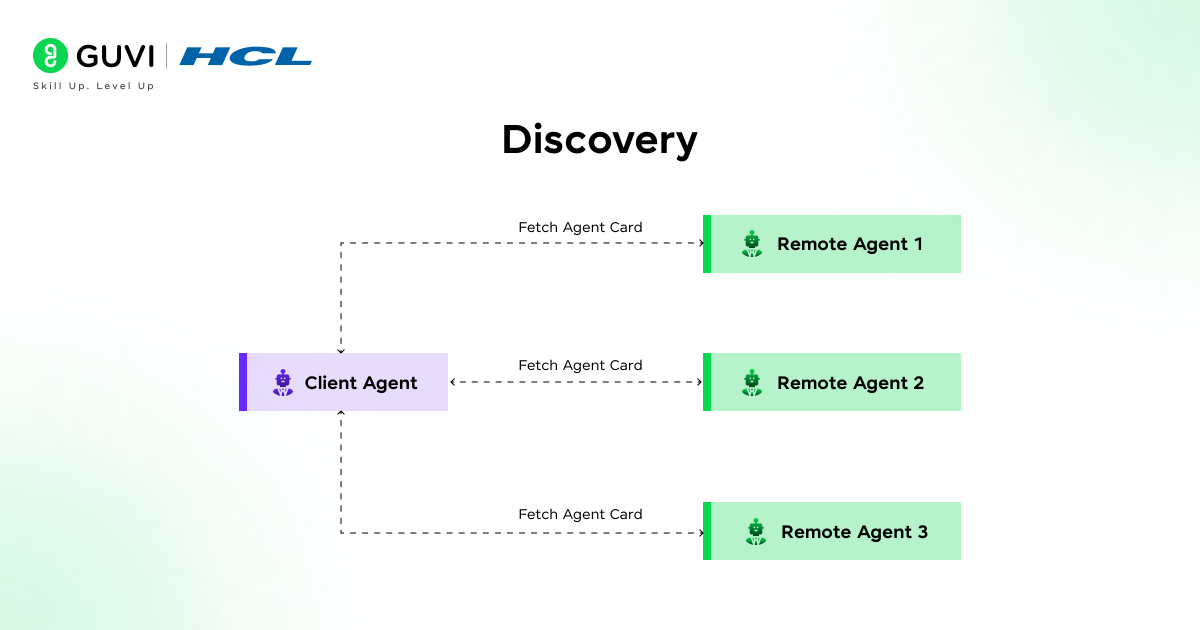
Discovery represents the stage where an agent identifies the presence and availability of another agent. The protocol defines how agents broadcast or advertise their capabilities and how listening agents respond with compatibility signals. This step often relies on service registries or distributed directories that store metadata about agent functions and endpoints.
An agent queries the directory to locate another with the required capabilities. Protocols such as DNS-SD or custom service advertisements are integrated into this phase to streamline the lookup process. The discovery step reduces ambiguity and prevents misaligned interactions by providing a clear map of who can perform what role.
- Authentication
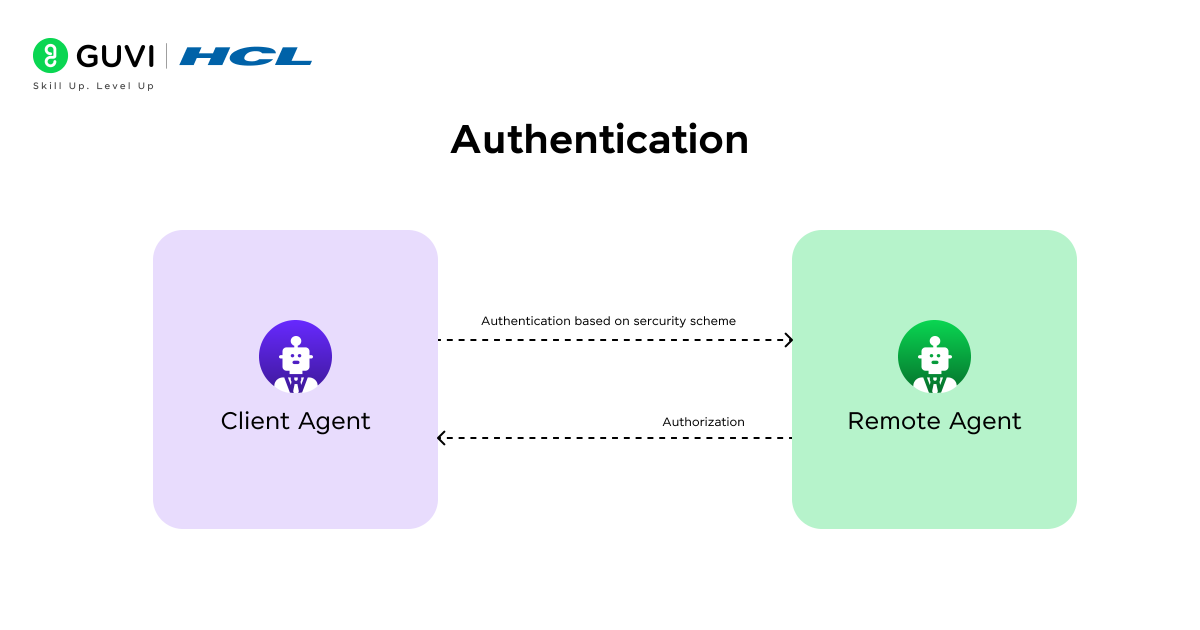
Authentication establishes trust between the two agents that were identified during discovery. Each agent verifies the other’s identity through cryptographic methods such as mutual TLS or token-based credentials issued by an authority. This prevents unauthorized agents from impersonating trusted participants. The process includes challenge-response handshakes and verification of certificates or cryptographic signatures.
Agents can also rely on role-based or attribute-based access control policies defined by the organization or ecosystem. This step is critical because an agent may advertise powerful capabilities during discovery, but only authenticated agents are allowed to make use of them.
- Communication
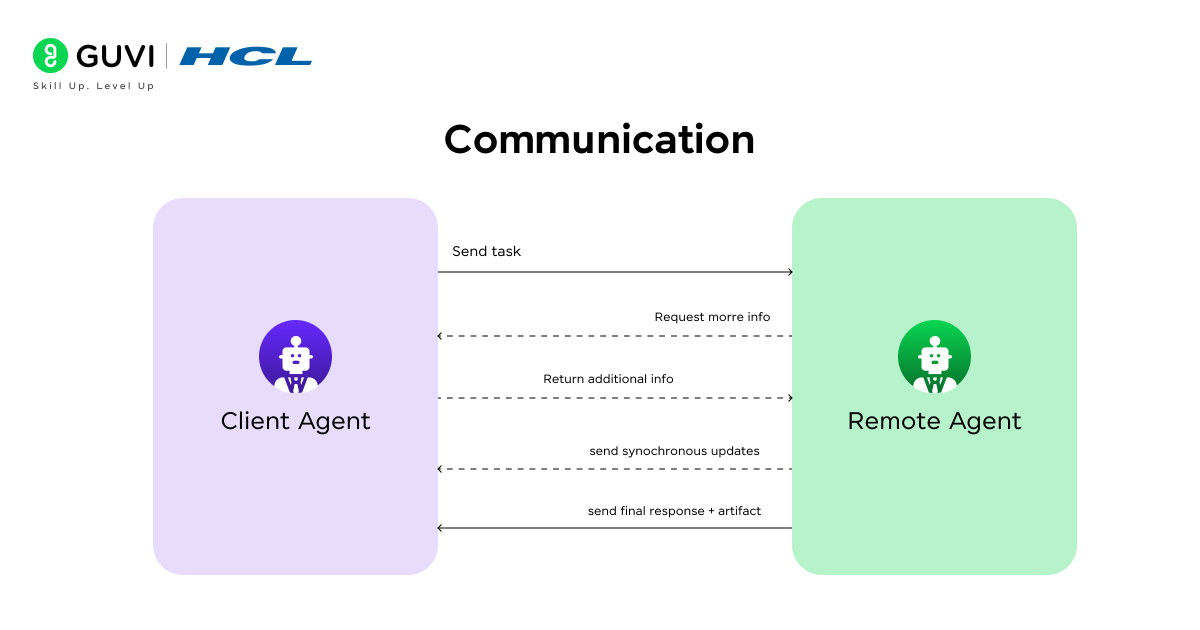
Communication begins once discovery and authentication are completed. The agents exchange data and coordinate tasks over secure channels established in the previous stage. The A2A protocol defines how messages are structured and interpreted. Messages can follow structured symbolic languages such as FIPA ACL or lightweight JSON schemas. Some agents also use vector embeddings when transmitting semantic context between large language model-driven systems.
Multiplexed streams in HTTP/2 or gRPC frameworks are often used to reduce latency and manage concurrent interactions. The communication stage can involve request-response cycles or negotiation dialogues. It may also involve cooperative task execution workflows. Reliability features such as retries and fault detection policies are integrated to maintain consistent performance.
Industrial Use Cases of the A2A Protocol
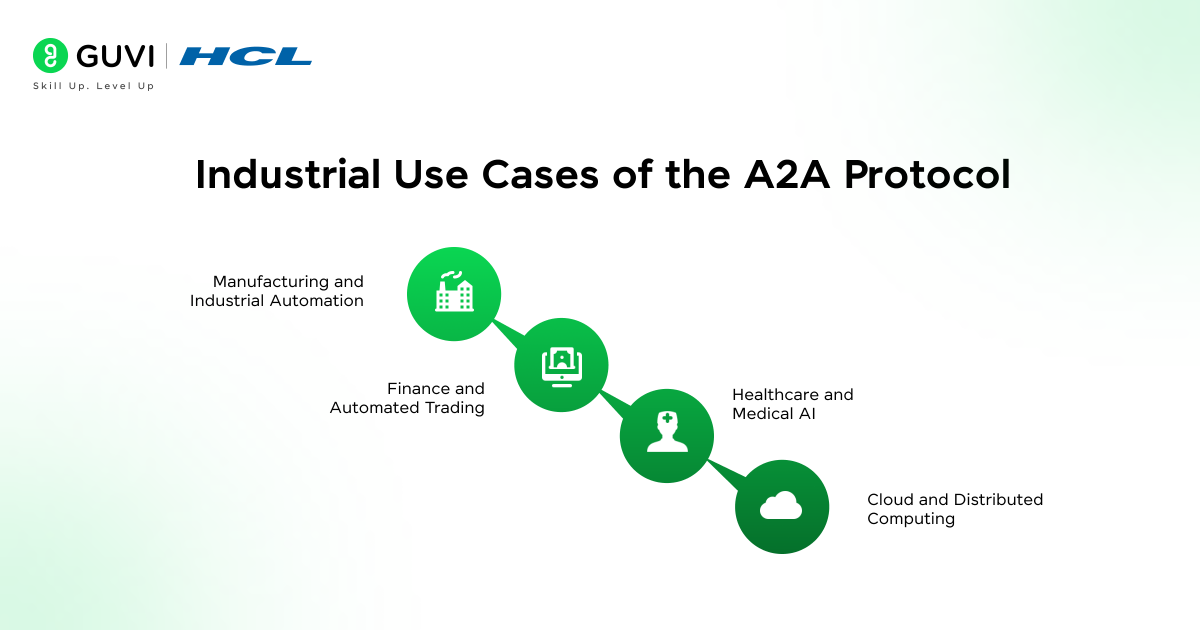
- Manufacturing and Industrial Automation
In modern factories, robotic systems and intelligent controllers need constant coordination. The A2A protocol provides a standardized way for robotic arms and inspection agents to share tasks without human intervention. A welding robot can request quality checks from a vision agent, and the vision agent can return validated inspection data. The result is a synchronized workflow where production lines adapt in real time to maintain efficiency.
- Finance and Automated Trading
Financial systems benefit from secure and rapid agent communication. Trading agents use the A2A protocol to negotiate bids and verify transaction integrity. Fraud detection agents can exchange suspicious activity alerts across institutions. This layered agent interaction helps financial organizations maintain speed and precision while protecting against risks in highly volatile markets.
Hospitals and medical research facilities are adopting agent-based ecosystems for diagnostics and treatment planning. Through A2A, diagnostic agents can forward test results to analysis agents, which then communicate recommended treatment options to care coordination agents. Secure authentication mechanisms in the protocol safeguard sensitive health data while supporting collaboration between specialized medical systems.
- Cloud and Distributed Computing
Cloud infrastructures and edge systems rely on diverse AI services operating together. The A2A protocol allows workload allocation agents and scaling agents to coordinate resource usage across distributed environments. An edge device can request computational support from a cloud-based processing agent, while monitoring agents report anomalies to administrative systems. This maintains efficiency across hybrid cloud computing ecosystems.
Difference Between MCP and A2A
MCP (Model Context Protocol) and A2A (Agent-to-Agent protocol) serve distinct purposes in AI-driven ecosystems. MCP focuses on extending the context and functionality of language models by connecting them with external tools and structured data sources. A2A centers on direct interactions between autonomous agents that exchange information, authenticate identities, and coordinate tasks. The table below outlines the main differences.
| Factor | MCP (Model Context Protocol) | A2A (Agent-to-Agent Protocol) |
| Primary Purpose | Connects language models with external data sources and tools | Establishes structured communication between autonomous agents |
| Architecture | Acts as a bridge between LLMs and resources | Follows a client-server model with discovery, authentication, and communication steps |
| Communication Mode | Model requests context or executes functions from external systems | Agents exchange messages, negotiate, and coordinate tasks |
| Security | Relies on access control to external data and APIs | Implements mutual authentication, cryptographic validation, and trust policies |
| Scope | Enhances reasoning and context retrieval for a single AI model | Builds interaction workflows across multiple autonomous agents |
| Typical Use Cases | Retrieval-augmented generation, tool invocation, structured context integration | Multi-agent coordination, federated AI workflows, swarm intelligence, and robotic collaboration |
Read: Top Artificial Intelligence Project Ideas for Students [2025]
Future of the Agent-to-Agent (A2A) Protocol in AI
The trajectory of the Agent-to-Agent (A2A) protocol is closely tied to the growth of multi-agent ecosystems and the demand for scalable autonomy. Its future lies in improving interoperability and adapting to increasingly complex environments. The main prospects include:
- Integration with Autonomous Infrastructure
The next stage of A2A adoption will align with cloud-native and edge-based infrastructures. Agents distributed across global networks will rely on A2A to balance workloads and optimize data exchange. This integration will reduce latency in applications such as autonomous vehicles and industrial automation. The protocol will serve as the backbone for decentralized orchestration of AI-driven infrastructures.
- Advanced Security and Trust Layers
As malicious agents become more sophisticated, A2A must incorporate advanced trust mechanisms. Future security layers will extend beyond traditional cryptography to include zero-trust policies and ledger-based audit trails. These enhancements will allow agents to confirm authenticity and establish reputation scores in large societies where trust is a scarce resource.
- Enabling Human-Agent Collaboration
A2A will not remain limited to machine-only ecosystems. It is likely to become a bridge between autonomous agents and human decision-makers. Structured protocols will allow agents to explain decisions and provide interpretable artifacts for human validation. This human-agent collaboration will be vital in regulated sectors like medicine, finance, and law, where accountability cannot be sacrificed.
Conclusion
The A2A protocol is a foundation for scalable and collaborative AI ecosystems where autonomous agents operate with precision and trust. Right from manufacturing floors to distributed cloud systems, it brings order to complexity and creates the conditions for future AI societies. The organizations that start preparing for A2A today will be the ones ready to lead in a future where intelligent agents are no longer isolated but interconnected in ways that drive real-world impact.
FAQs
1. How does the A2A protocol improve multi-agent collaboration?
The A2A protocol provides a structured framework that reduces ambiguity in agent communication. Agents exchange messages with shared semantics, which allows them to negotiate goals and coordinate tasks effectively. This structured interaction improves alignment in multi-agent environments and supports both cooperative and competitive workflows.
2. Why is security central to A2A protocol design?
Security is critical because autonomous agents often handle sensitive data or execute high-value operations. The A2A protocol integrates authentication and access control policies. These measures prevent impersonation and block unauthorized requests.
3. What role do agent cards play in A2A ecosystems?
Agent cards act as digital profiles that describe agent capabilities and supported services. They provide the metadata required for discovery and negotiation.
4. How is A2A applied in cloud and distributed AI systems?
In distributed infrastructures, multiple AI services operate across cloud and edge environments. The A2A protocol standardizes communication between workload allocation agents and scaling agents. This coordination improves resource utilization and allows hybrid systems to function as unified ecosystems.
5. What makes A2A different from traditional enterprise communication protocols?
Enterprise protocols such as application-to-application (A2A) systems focus on fixed workflows between predefined services. The Agent-to-Agent protocol in AI is designed for autonomous entities that adapt and make independent decisions. Its purpose is to support emergent coordination in environments where agents must respond to changing objectives and conditions.


























Did you enjoy this article?