
Security & PHP: What Modern PHP Developers Need to Know
Feb 04, 2026 4 Min Read 430 Views
(Last Updated)
PHP security is a critical requirement for modern web applications, not an optional add-on. Today, PHP powers APIs, SaaS platforms, content management systems, eCommerce websites, and enterprise applications, all of which handle sensitive user data. Due to its widespread use, PHP security has become a primary focus for developers seeking to build reliable and trustworthy systems.
This blog covers essential PHP security concepts, common vulnerabilities, and best practices that modern developers must follow when building real-world applications. It is designed for beginners, students, working PHP developers, and anyone who wants to understand how to write secure PHP code and protect applications from security threats.
Quick Answer
PHP security focuses on preventing common vulnerabilities, protecting user data, securing databases and authentication, and using modern PHP features to build safe and reliable web applications.
Table of contents
- Why Security Matters In Modern PHP Development
- Common Security Threats PHP Developers Must Know
- Input Validation And Output Escaping
- Secure Database Interaction
- Authentication And Password Security
- Protecting Against CSRF And XSS Attacks
- File Upload And Server Security
- Using Modern PHP Features And Frameworks
- Logging, Monitoring, And Error Handling
- 💡 Did You Know?
- Conclusion
- FAQs
- Is PHP secure for modern web applications?
- Do PHP frameworks improve security?
- How often should PHP applications be updated?
- Is manual security testing necessary?
Why Security Matters In Modern PHP Development
Modern PHP applications handle sensitive user data, authentication, and core business logic, making security an essential part of development. Since PHP is widely used across websites and APIs, insecure applications are more exposed to common security attacks.
Ignoring PHP security can lead to data breaches, unauthorized access, and loss of user trust. Even small coding mistakes can create serious vulnerabilities, which is why secure coding practices are critical in modern PHP development.
Key Points
• Sensitive Data Handling
PHP applications process personal and login data that must be protected from leaks and misuse.
• High Attack Exposure
The widespread use of PHP makes applications common targets for automated security attacks.
• Small Mistakes, Big Risks
Minor issues like poor input validation or weak authentication can lead to major vulnerabilities.
• User Trust And Compliance
Strong PHP security helps maintain user confidence and meet compliance requirements.
Do check out HCL GUVI’s Learn PHP course, which focuses on core PHP development skills such as working with server-side logic, handling user input, managing sessions and cookies, and building dynamic web applications. These fundamentals are directly relevant to understanding PHP security, as secure coding starts with knowing how PHP handles data, user interactions, and backend workflows in real-world applications.
Common Security Threats PHP Developers Must Know
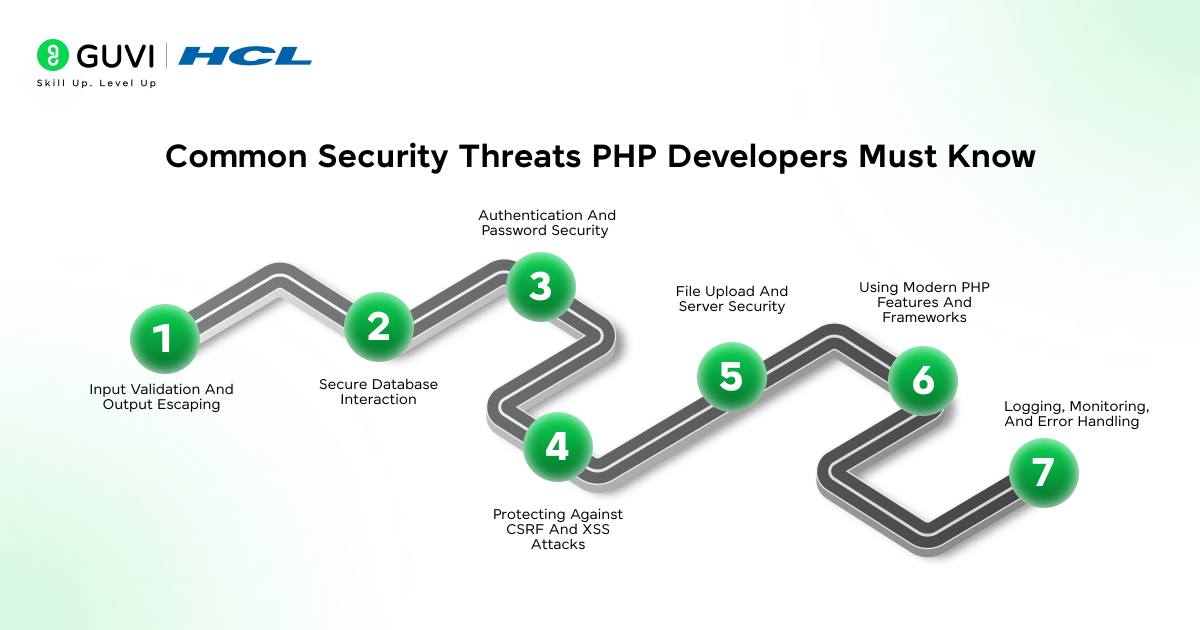
Understanding PHP security threats helps developers prevent vulnerabilities before they are exploited. Below are the detailed explanations with key points under each subheading.
1. Input Validation And Output Escaping
Input validation and output escaping are fundamental to PHP security because user-supplied data is one of the most common attack vectors. Attackers often inject malicious input through forms, URLs, or headers to manipulate application behavior. Proper validation ensures data meets expected rules, while output escaping prevents malicious scripts from executing in the browser. Together, these practices reduce risks such as cross-site scripting and data manipulation.
Key Points
• Validate Input
Check input based on type, length, and format to ensure it meets expected criteria.
• Never Trust User Data
Data from forms, URLs, cookies, and headers must always be sanitized.
• Escape Output
Escape any user-generated content before displaying it to prevent XSS attacks.
• Use Built-in Filters
PHP provides filtering functions to handle input safely and consistently.
2. Secure Database Interaction
Databases store critical application data, making them prime targets for attacks such as SQL injection. Insecure queries can allow attackers to read, modify, or delete sensitive information. Secure database interaction focuses on isolating user input from SQL logic and limiting database access. These practices help ensure data integrity and reduce the impact of potential breaches.
Key Points
- Use Prepared Statements – Avoid raw queries with user input; use prepared statements to prevent SQL injection.
- Limit Database Permissions – Grant only necessary permissions to reduce the potential impact of a breach.
- Avoid Dynamic Queries – Do not build SQL queries directly from user input.
- Secure Credentials – Store database credentials safely using environment variables.
3. Authentication And Password Security
Authentication systems control access to PHP applications and must be designed with strong security measures. Weak password storage or session handling can allow attackers to impersonate users. Proper authentication practices focus on secure password storage, session protection, and abuse prevention. These measures ensure that only authorized users gain access.
Key Points
- Hash Passwords – Use secure PHP hashing algorithms to store passwords.
- Never Store Plain Text – Storing passwords in plain text is a critical security flaw.
- Limit Login Attempts – Prevent brute force attacks by restricting repeated failed logins.
- Secure Sessions – Regenerate session IDs and use secure session handling practices.
4. Protecting Against CSRF And XSS Attacks
CSRF and XSS attacks exploit the trust between users and applications. CSRF tricks authenticated users into performing unintended actions, while XSS injects malicious scripts into web pages. Preventing these attacks requires validating request authenticity and carefully handling output. These protections are essential for browser-based PHP applications.
Key Points
- CSRF Tokens – Use tokens for all state-changing requests and validate them on the server.
- Escape HTML Output – Prevent script injection by escaping all user-generated content.
- Set Secure Headers – Use HTTP headers like Content Security Policy (CSP) to enhance security.
5. File Upload And Server Security
File uploads introduce serious security risks if not handled carefully. Attackers may upload malicious files to execute code or access server resources. Secure file handling focuses on strict validation, controlled storage, and limited permissions. These steps help protect the server and application environment.
Key Points
- Validate Files – Check file types and sizes before accepting uploads.
- Store Securely – Keep uploads outside public directories to prevent execution.
- Rename Files – Rename uploads to avoid malicious execution.
- Restrict Permissions – Set strict permissions to limit access.
6. Using Modern PHP Features And Frameworks
Modern PHP versions and frameworks include built-in security improvements that reduce common vulnerabilities. Using outdated versions exposes applications to known exploits. Leveraging modern tools allows developers to rely on secure defaults rather than building custom solutions. Regular updates are a key part of long-term PHP security.
Key Points
- Update PHP – Always run the latest stable version.
- Use Secure Frameworks – Frameworks with built-in security features reduce risk.
- Leverage Built-in Helpers – Use native helpers instead of custom implementations.
- Update Dependencies – Regularly patch dependencies to fix vulnerabilities.
7. Logging, Monitoring, And Error Handling
Logging and monitoring help identify security incidents early and reduce damage. Poor error handling can expose sensitive system information to attackers. Proper logging practices balance visibility with confidentiality. This ensures issues are detected without revealing internal details.
Key Points
- Log Suspicious Activity – Track authentication failures and unusual behavior.
- Avoid Detailed Errors – Do not expose sensitive information in error messages.
- Environment-Based Reporting – Use appropriate error reporting depending on the production or development environment.
- Regular Log Review – Monitor logs to identify anomalies quickly.
💡 Did You Know?
- Many PHP security vulnerabilities come from outdated PHP versions rather than the language itself
- PHP provides built in functions for password hashing and input filtering that are often underused
- Most large scale PHP breaches happen due to misconfigured servers, not core PHP flaws
Conclusion
PHP security is not a one-time setup but a continuous responsibility for modern developers. As applications grow in complexity, security risks also evolve, making it essential to follow secure PHP coding practices throughout the development lifecycle.
By focusing on PHP security best practices such as input validation, secure authentication, database protection, and regular updates, developers can build applications that are resilient, trustworthy, and ready for real-world use.
FAQs
1. Is PHP secure for modern web applications?
Yes, PHP is secure when developers follow best practices, use updated versions, and implement proper security measures.
2. Do PHP frameworks improve security?
Most modern frameworks provide secure defaults and built-in protection, but developers must still write secure code.
3. How often should PHP applications be updated?
PHP versions, frameworks, and dependencies should be updated regularly to fix known vulnerabilities.
4. Is manual security testing necessary?
Yes, regular testing helps identify issues that automated tools may miss.

































Did you enjoy this article?