Learn Ethical Hacking, Network Security, Mobile Hacking & Application Security through hands-on, project-based training from expert instructors. 2,000+ students are already launching their cybersecurity careers.
9+
Years of Experience
250+
Certifications
49K
Students Enrolled
4.4 ⭐️
Google Reviews (10,643)
All-in-One Web Design Mastery!
Learn Ethical Hacking, Network Security, Mobile Hacking & Application Security through hands-on, project-based training from expert instructors. 2,000+ students are already launching their cybersecurity careers.
The HCL GUVI Cybersecurity Bundle gives you complete access to a comprehensive cybersecurity learning path. Master Ethical Hacking, Network Security, Mobile & Application Security, Penetration Testing, and more. Learn at your own pace, build hands-on skills, gain globally recognized certifications, and prepare for high-paying roles in cybersecurity.
5K people registered already!
The HCL GUVI Cybersecurity Bundle gives you complete access to a comprehensive cybersecurity learning path. Master Ethical Hacking, Network Security, Mobile & Application Security, Penetration Testing, and more. Learn at your own pace, build hands-on skills, gain globally recognized certifications, and prepare for high-paying roles in cybersecurity.
5K people registered already!
Students
Who want to learn tech early, build strong fundamentals, and earn certificates that add weight to their resume.
Freshers
Who need job-ready skills, projects, and a portfolio to stand out during placement drives and interviews.
Working Professionals
Who are looking for a salary hike, skill upgrade, or career growth by mastering in-demand technologies.
Career Switchers
From both tech and non-tech backgrounds who want to transition into a high-growth tech career with practical, industry-aligned learning.
7-Day Money-Back
Instant Access
Lifetime Access
Free Certificates
Instant Access
Lifetime Access
Free Certificates
Instant Access
Lifetime Access
Cyber Security Bundle Curriculum
What You Will Learn in the Web Design Bundle
Limited Period Offer
Each time you complete a course in the Cybersecurity Bundle, you’ll receive a professional certificate issued by HCL GUVI (an IIT-M & IIM-A incubated EdTech company). All certificates are ISO-certified, globally recognized, and shareable on LinkedIn and resumes, helping you showcase your skills, boost your profile, and stand out to recruiters.
Each time you complete a course, you’ll receive a professional certificate issued by HCL GUVI (an IIT-M & IIM-A incubated EdTech company). All certificates are ISO-certified, industry-recognized, and easily shareable on LinkedIn and in your resume, helping you enhance your profile and stand out to recruiters.
Industry-Recognized Credentials
Get certificates that are valued by recruiters and tech companies.
Shareable on LinkedIn
Add every completed-course certificate to LinkedIn and impress potential employers with consistent growth.
Proof of Real Skills
Every certificate reflects practical knowledge and tools you’ve mastered — evidence of real, job-ready skills.
Resume-Ready Format
Download each certificate instantly and attach it to job applications, portfolios, and resumes effortlessly.
Each time you complete a course in the Cybersecurity Bundle, you’ll receive a professional certificate issued by HCL GUVI (an IIT-M & IIM-A incubated EdTech company). All certificates are ISO-certified, globally recognized, and shareable on LinkedIn and resumes, helping you showcase your skills, boost your profile, and stand out to recruiters.
Industry-Recognized Credentials
Get certificates that are valued by recruiters and tech companies.
Shareable on LinkedIn
Add every completed-course certificate to LinkedIn and impress potential employers with consistent growth.
Proof of Real Skills
Every certificate reflects practical knowledge and tools you’ve mastered — evidence of real, job-ready skills.
Resume-Ready Format
Download each certificate instantly and attach it to job applications, portfolios, and resumes effortlessly.
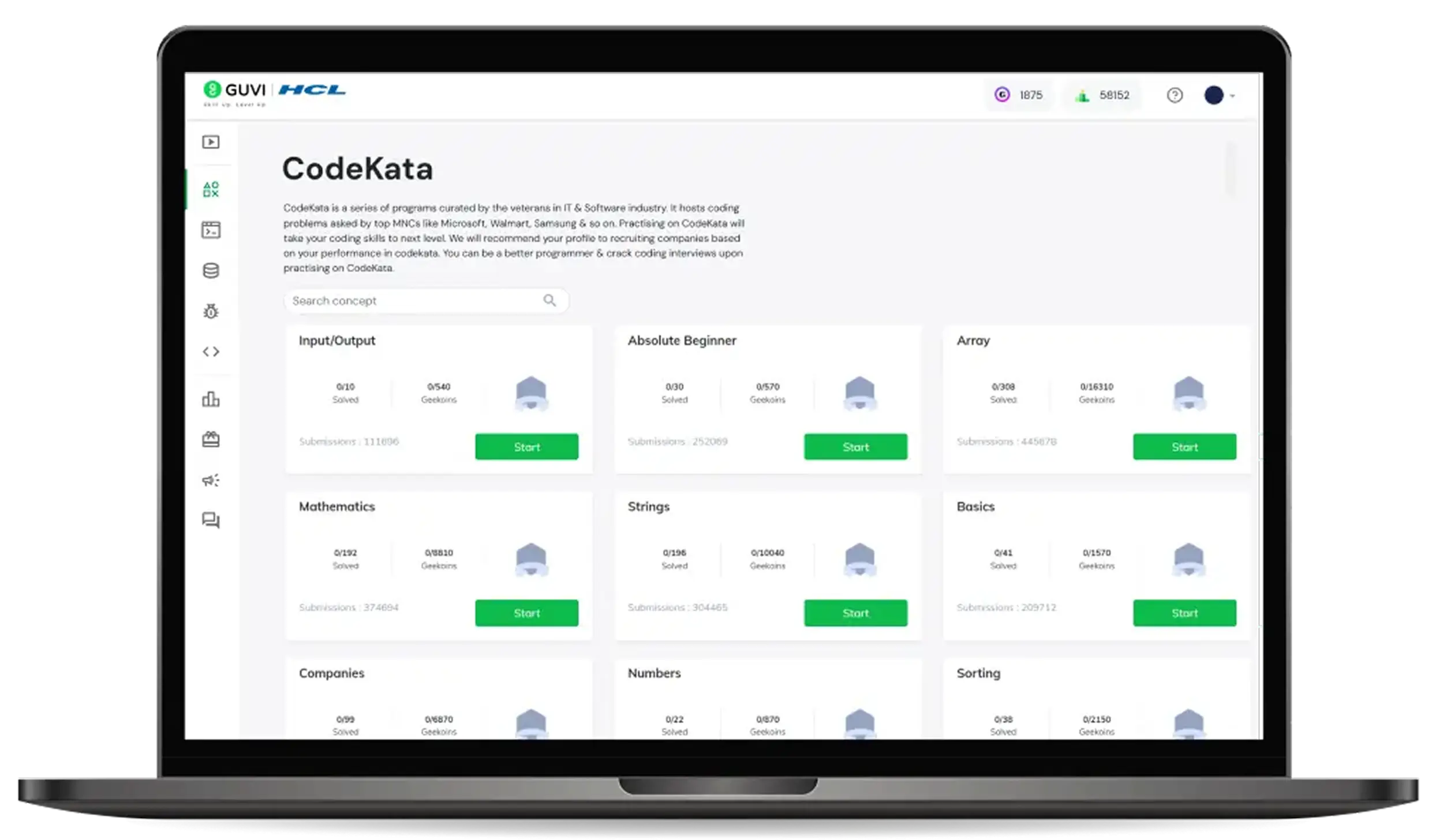
CodeKata
An interactive coding platform with 1500+ curated problems by IT experts. CodeKata tracks your progress and builds a coding profile to highlight your skills for job opportunities.
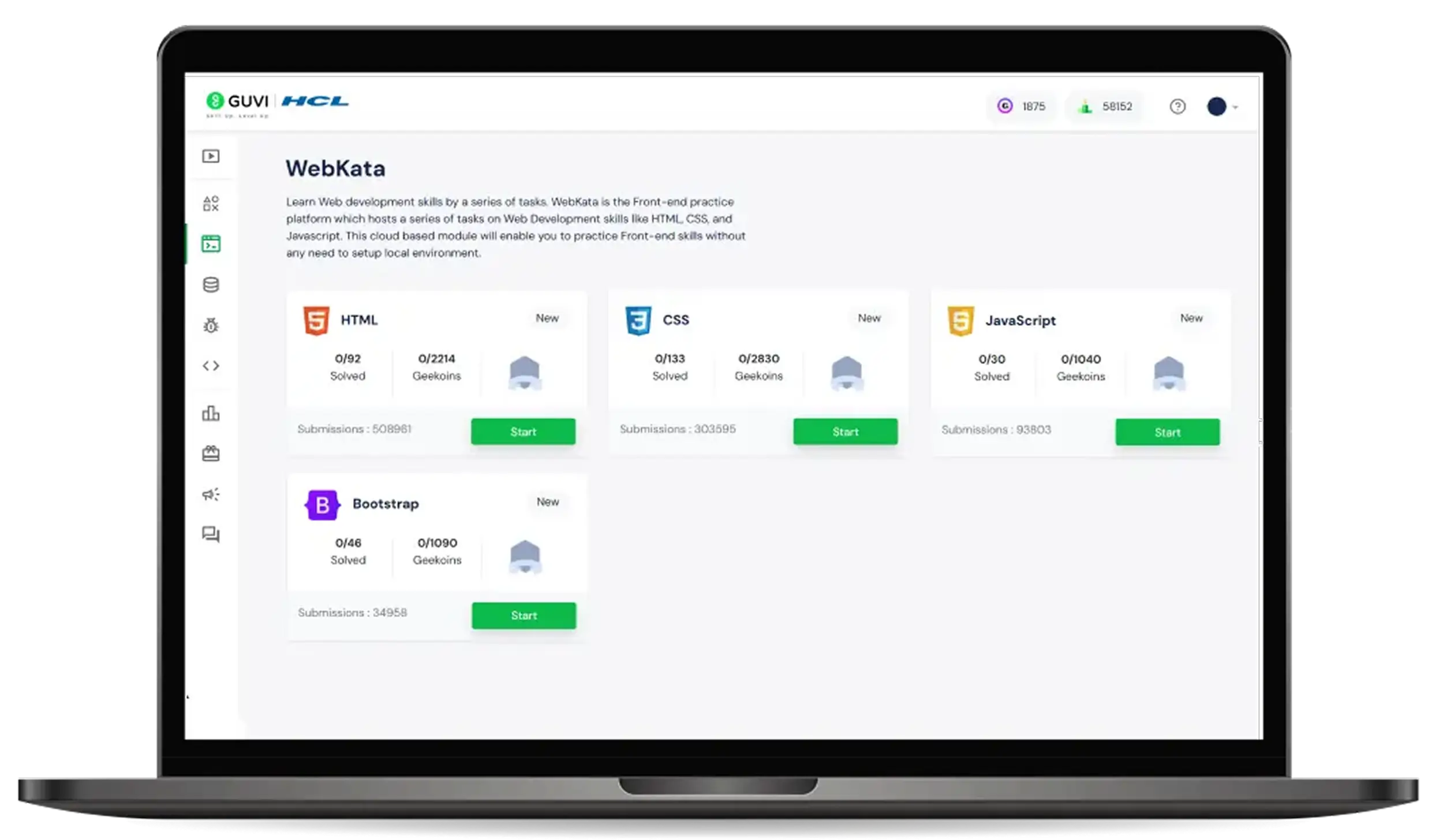
WebKata
WebKata is a developing practice platform for beginners, built with top-notch web development problem statements focusing on Modern HTML, CSS, and JavaScript.
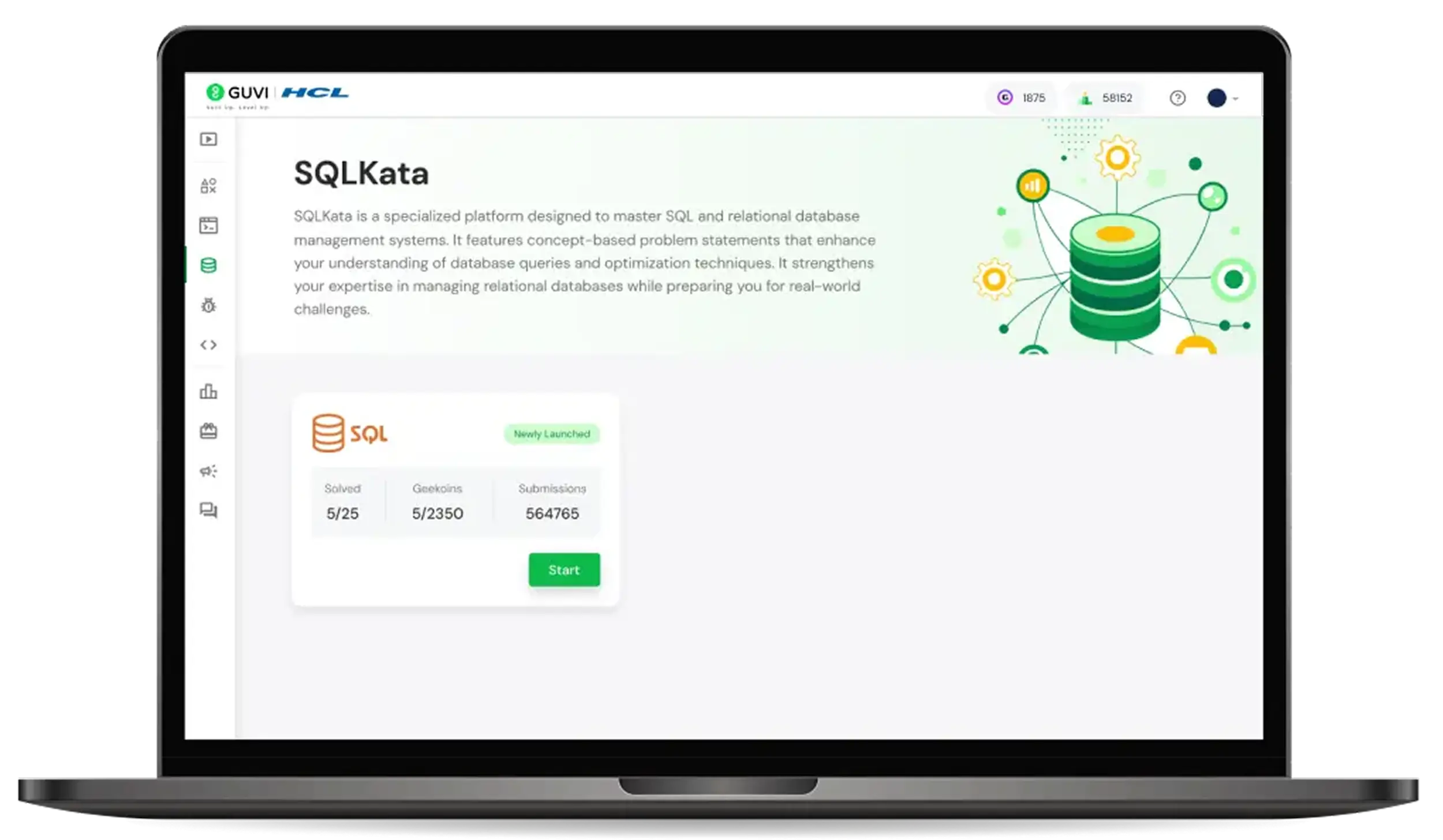
SQLKata
SQLKata is a hands-on tool to master SQL through concept-driven exercises. It builds skills in query writing, optimization, and real-world database management.
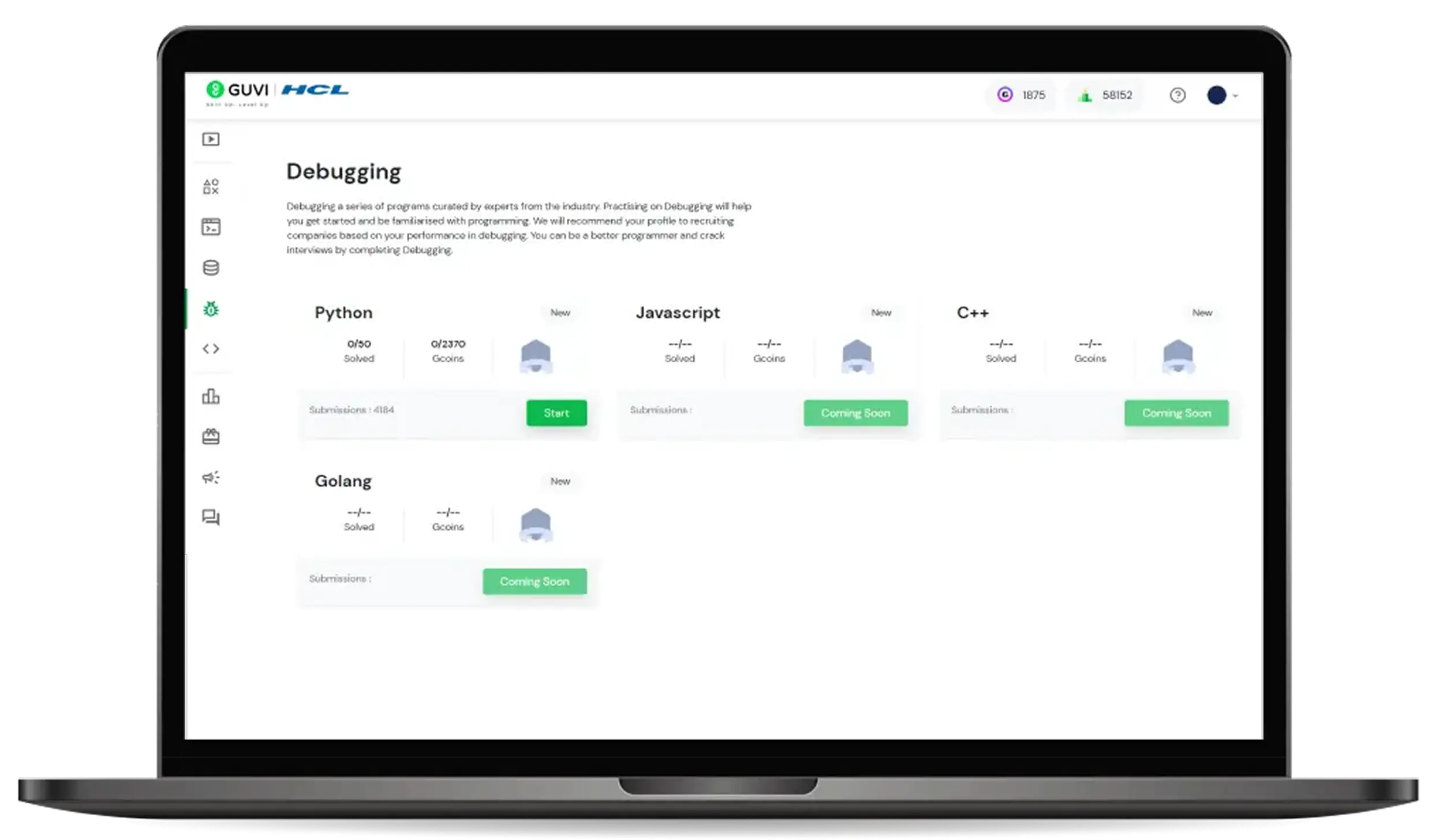
Debugging
Debugging a series of programs curated by industry experts. Practicing debugging will help you get started and become familiar with programming.
Real Stories. Real Outcomes.
"You will be lucky to find quality courses on HCL GUVI. I must say that I was really lucky to get courses at such a low and discounted price. I got more than 9 hours of video and around 20 more resources to gain knowledge of programming. HCL GUVI provides a wide variety of courses both technical and non-technical. I suggest HCL GUVI is the best choice."
"What makes HCL GUVI different is that it provides vernacular courses which make it easy to understand & practice platforms like CodeKata & WebKata, all these helped me improve my practical programming skills in the front end, back end. I highly recommend it if you want to get started with something new."
"I have opted for a combo-course that starts with the basics of the popular technologies and made me a pro in its domain... Codekata is very damn helpful to crack placements because it improved my efficiency in coding... we just need to be persistent and that’s all it takes. I am very happy to encounter HCL GUVI!"
You’ll get full access to all our cybersecurity courses — from Ethical Hacking to Network, Mobile, and Web Security. Every course comes with hands-on labs, real projects, expert support, and certificates when you finish.
Nope! It’s a one-time payment of ₹1999. No hidden or recurring fees.
You’ll have lifetime access — learn at your own pace, anytime, anywhere.
Yes! Every course you complete gives you a globally recognized certificate that you can show on your LinkedIn profile or resume.
All lessons are pre-recorded, so you can study whenever it fits your schedule — mornings, evenings, or weekends.
Absolutely. The bundle includes hands-on labs, real-world projects, and CTF challenges so you can actually apply your skills.
No problem! There’s a 7-day money-back guarantee. If it’s not right for you, just request a refund within the first week.
Get unlimited access to 600+ Premium Tech Courses for just
Save 80% and learn the most in-demand skills that can fast-track your tech career!
Limited Period Offer
Limited Period Offer
Get unlimited access to the complete Cybersecurity Bundle
Limited Period Offer
Get unlimited access to 600+ Premium Tech Courses for just
Save 80% and learn the most in-demand skills that can fast-track your tech career!
Limited Period Offer
Maltego - Discovering Websites Hosting Provider Emails
What are they And How To Discover Exploit Basic File Upload Vulnerabilities
HTTP Requests - GET - POST
Intercepting HTTP Requests
Exploiting Advanced File Upload Vulnerabilities
Exploiting More Advanced File Upload Vulnerabilities
Security Fixing File Upload Vulnerabilities
What are they How To Discover Exploit Basic Code Execution Vulnerabilities
Exploiting Advanced Code Execution Vulnerabilities
Security - Fixing Code Execution Vulnerabilities
What is SQL?
Dangers of SQL Injections
Discovering SQL Injections In POST
Bypassing Logins Using SQL Injection Vulnerability
Bypassing More Secure Logins Using SQL Injections
Security Preventing SQL Injections In Login Pages
Discovering Exploiting Blind SQL Injections
Discovering SQL Injections And Extracting Data Using SQLmap
Getting a Direct SQL Shell using SQLmap
Introduction - What is XSS or Cross Site Scripting
Discovering Basic Reflected XSS
Discovering Advanced Reflected XSS
Discovering An Even More Advanced Reflected XSS
Discovering Stored XSS
Discovering Advanced Stored XSS
Hooking Victims To BeEF Using Stored XSS
Hooking Targets With Beef
Capturing ScreenShot Of Target
Redirecting Target To Any Website
Force Target To Watch Youtube Video
Steal FacebookGmail Password Using Beef