Become a Professional Ethical hacker Today!
Cyber Security Course Features
6 Courses
Individual Certifications
2000+
Enrolled
25+ Hours
Recorded Content (100% Online)
Lifetime Access
One-time Purchase
Forum Support
Doubt Clarification
Quiz & Assessments
In All Modules
7 Days
Refund Policy
Cyber Security Course Features
6 Courses
Individual Certifications
25+ Hours
Recorded Content (100% Online)
2000+
Enrolled
Lifetime Access
One-time Purchase
Forum Support
Doubt Clarification
Quiz & Assessments
In All Modules
7 Days
Refund Policy
Cyber Security Bundle Curriculum
Grab Our Exclusive 80% OFF Cybersecurity Combo Deal Before It’s Gone!
Empower Your Cyber Skills Today!
Limited Period Offer
Grab Our Exclusive 80% OFF Cybersecurity Combo Deal Before It’s Gone!
Empower Your Cyber Skills Today!
Limited Period Offer
Why Choose GUVI?
Mentor Guidance
Stuck in your code? Our dedicated mentors guide you through every step via the active community forum.
Gamified Learning Experience
Learn Web Development with AI through coding challenges, quizzes, and projects that make learning fun, interactive, and rewarding.
Structured Learning Path
Follow a clear, beginner-friendly roadmap with step-by-step lessons, hands-on practice, and real-world AI-driven web projects.
Resume-Ready Certifications
Earn IITM Pravartak certifications for each tool and technology, and showcase verified skills on LinkedIn and your resume.
Certify Your Skills
Complete each course and earn 6 individual certificates — one for every cybersecurity specialization you master! Complete the modules and claim your certificates to enhance your resume and LinkedIn profile.
Dedicated Forum Support
Post Doubts Anytime
Get your questions answered quickly through our dedicated forum.
Quick Response
Most doubts are resolved within 5–10 minutes.
Mentor Support
Enjoy personal guidance from expert mentors to help you learn better and faster.
Build Skills That Boost Your Resume
Skill-Focused Courses
Resume-Ready Certifications
Stand Out in Applications
Gamified Learning Experience
Bonus Features You Get
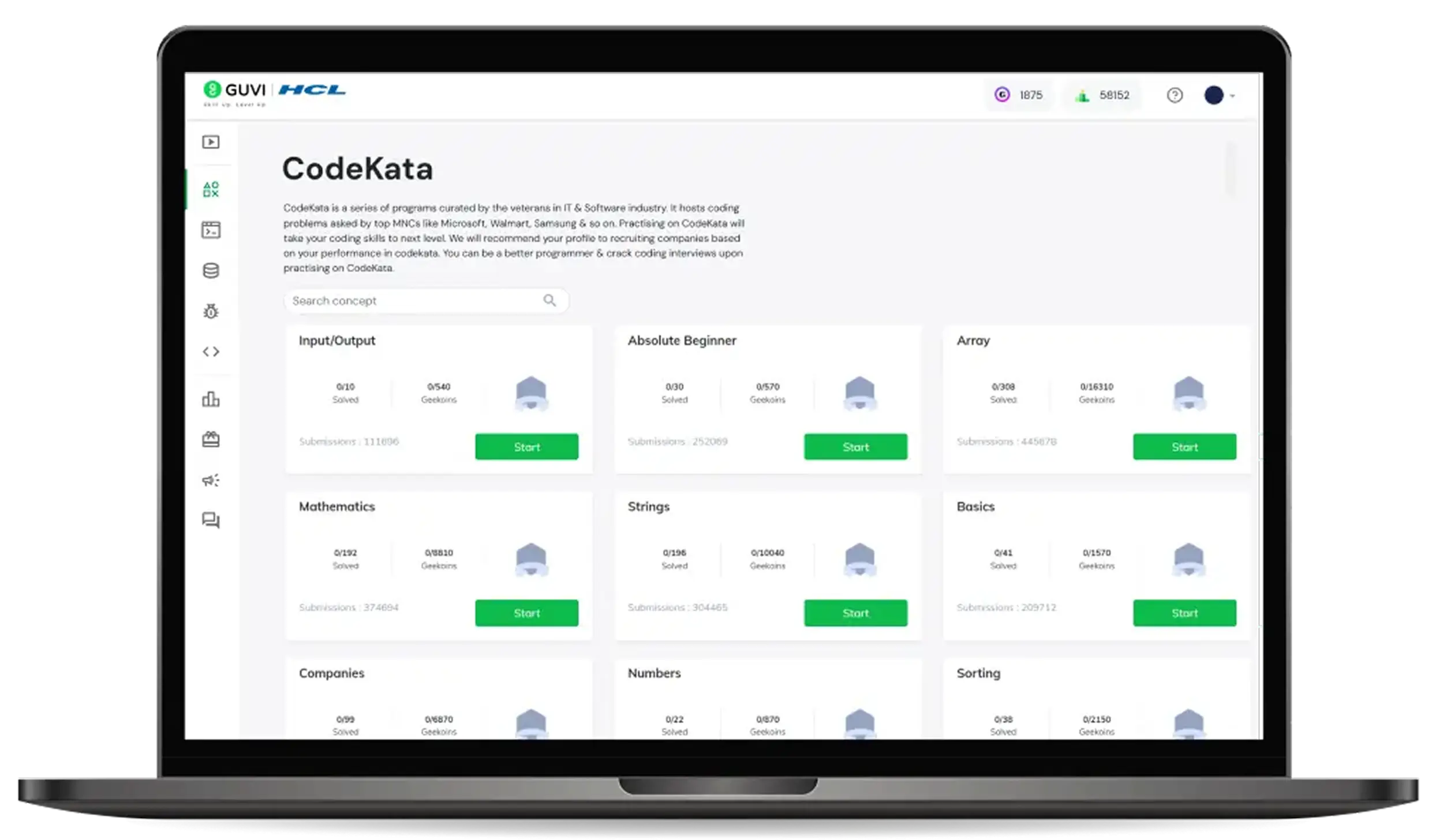
CodeKata
An interactive coding platform with 1500+ curated problems by IT experts. CodeKata tracks your progress and builds a coding profile to highlight your skills for job opportunities.
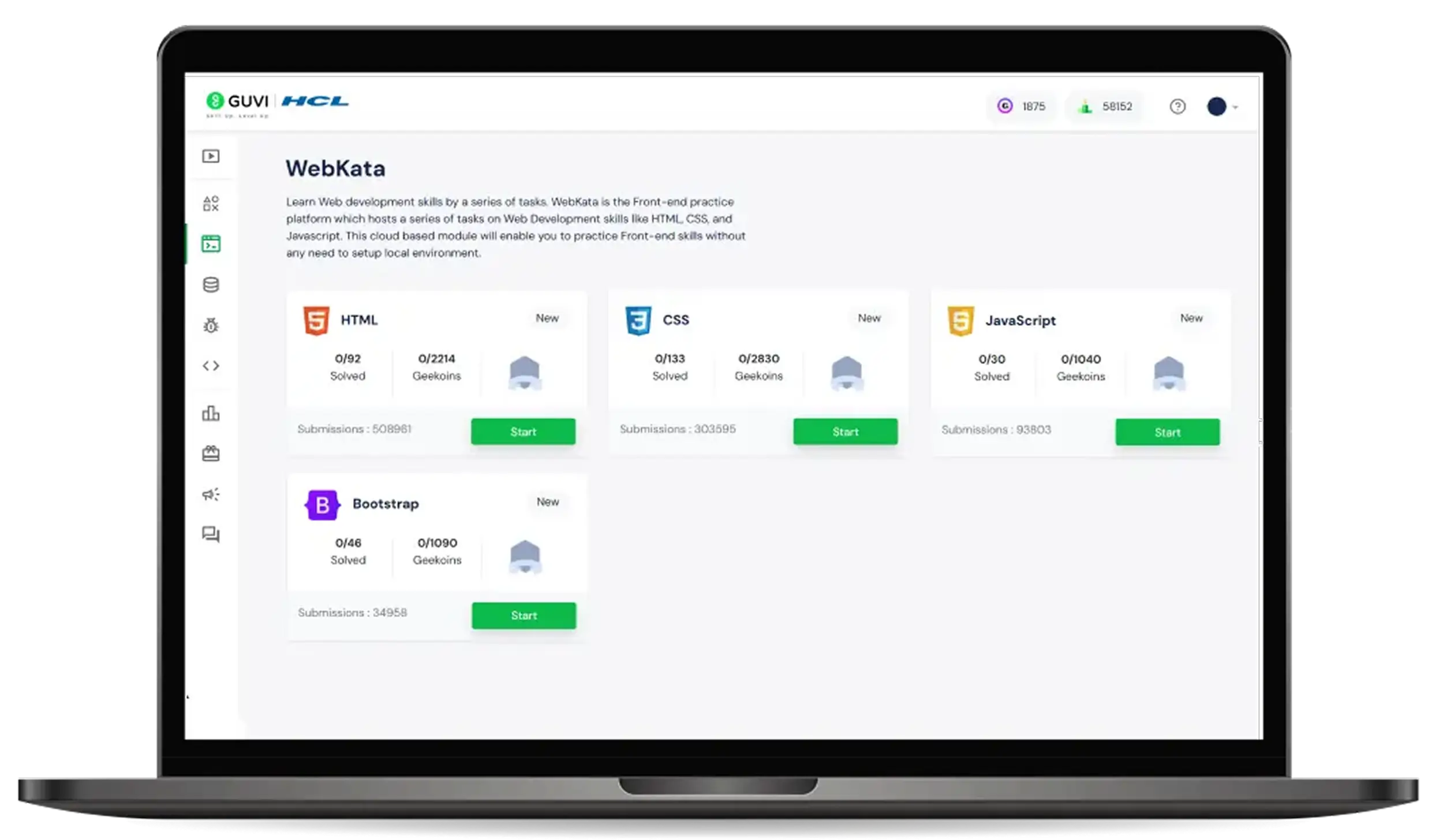
WebKata
WebKata is a developing practice platform for beginners, built with top-notch web development problem statements focusing on Modern HTML, CSS, and JavaScript.
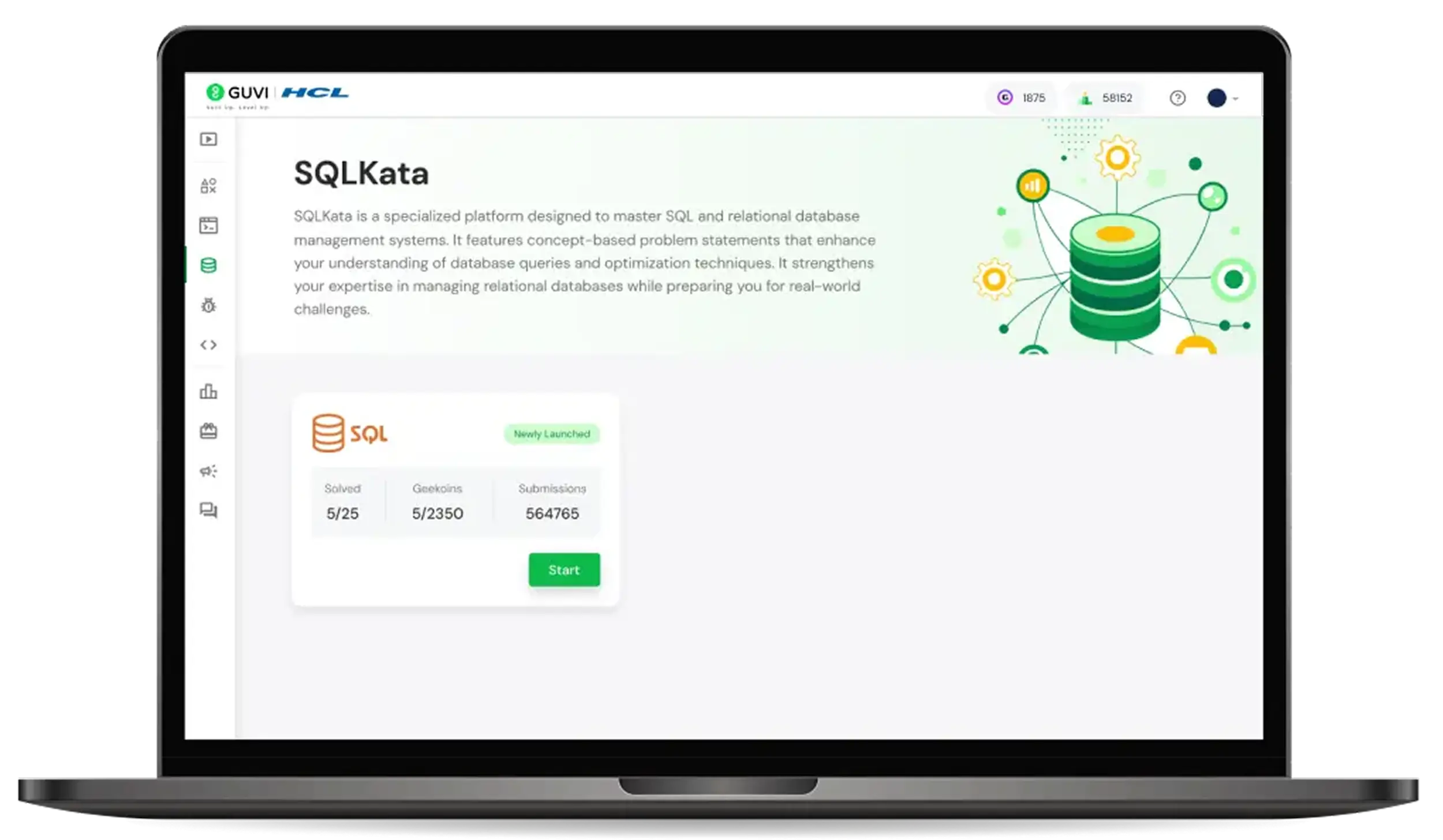
SQLKata
SQLKata is a hands-on tool to master SQL through concept-driven exercises. It builds skills in query writing, optimization, and real-world database management.
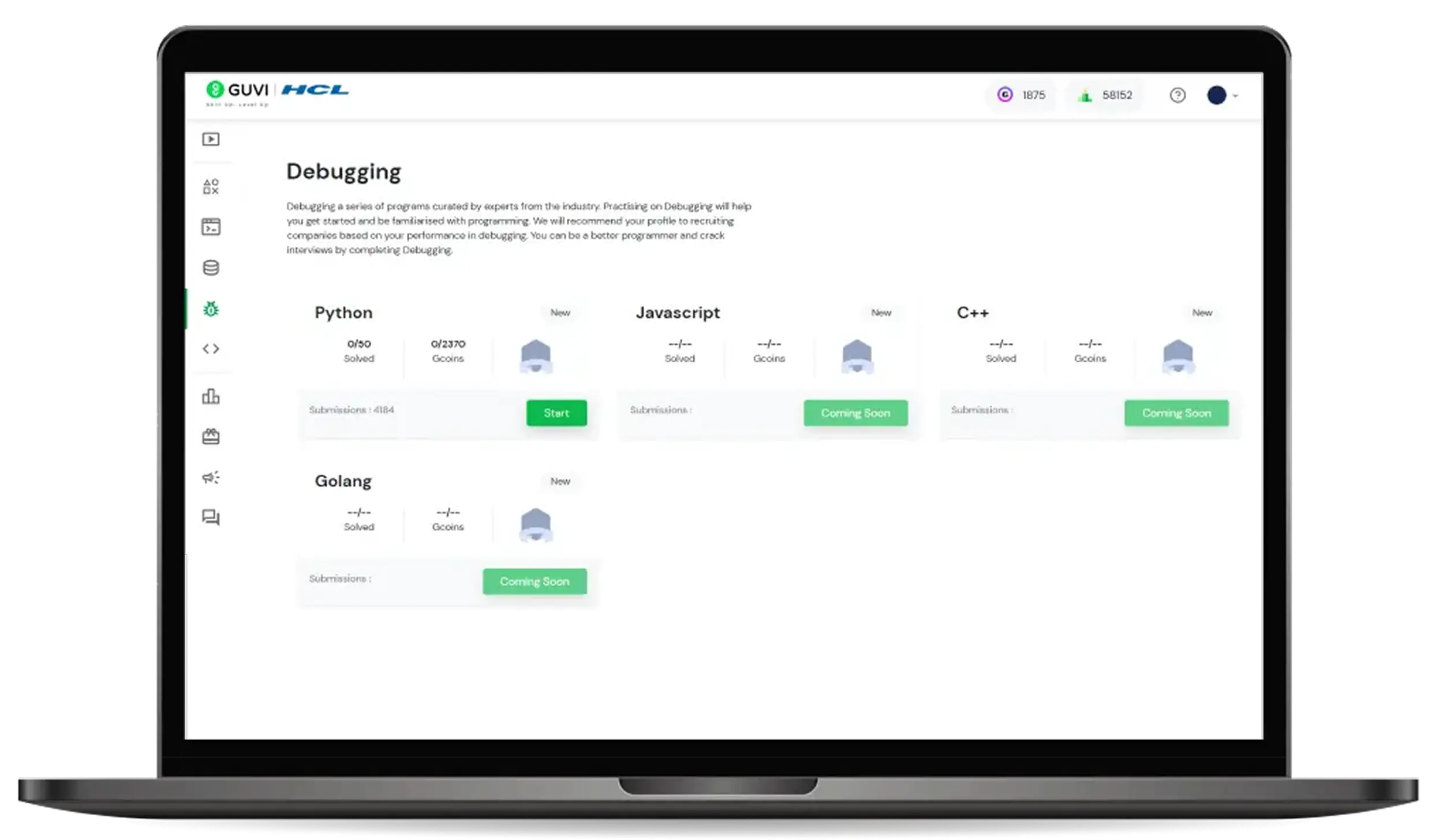
Debugging
Debugging a series of programs curated by industry experts. Practicing debugging will help you get started and become familiar with programming.
Real stories. Real outcomes.
Hear from learners who’ve transformed their productivity and career growth by mastering top AI tools with us!
"You will be lucky to find quality courses on GUVI. I must say that I was really lucky to get courses at such a low and discounted price. I got more than 9 hours of video and around 20 more resources to gain knowledge of programming. GUVI provides a wide variety of courses both technical and non-technical. I suggest GUVI is the best choice."
"What makes GUVI different is that it provides vernacular courses which make it easy to understand & practice platforms like CodeKata & WebKata, all these helped me improve my practical programming skills in the front end, back end. I highly recommend it if you want to get started with something new."
"I have opted for a combo-course that starts with the basics of the popular technologies and made me a pro in its domain... Codekata is very damn helpful to crack placements because it improved my efficiency in coding... we just need to be persistent and that’s all it takes. I am very happy to encounter GUVI!"
Real stories. Real outcomes.
Hear from learners who’ve transformed their productivity and career growth by mastering top AI tools with us!
"You will be lucky to find quality courses on GUVI. I must say that I was really lucky to get courses at such a low and discounted price. I got more than 9 hours of video and around 20 more resources to gain knowledge of programming. GUVI provides a wide variety of courses both technical and non-technical. I suggest GUVI is the best choice."
"What makes GUVI different is that it provides vernacular courses which make it easy to understand & practice platforms like CodeKata & WebKata, all these helped me improve my practical programming skills in the front end, back end. I highly recommend it if you want to get started with something new."
"I have opted for a combo-course that starts with the basics of the popular technologies and made me a pro in its domain... Codekata is very damn helpful to crack placements because it improved my efficiency in coding... we just need to be persistent and that’s all it takes. I am very happy to encounter GUVI!"
Course Details
In today’s digitally connected world, cybersecurity skills are no longer optional — they’re critical. The Cybersecurity Combo Bundle offers a practical, beginner-friendly path to mastering essential cybersecurity domains like Ethical Hacking, Network Security, Dark Web Intelligence, Mobile Hacking, and more. Designed for students, IT professionals, and tech enthusiasts, this bundle emphasizes real-world scenarios and hands-on skills that are in high demand across industries. With short, engaging video lessons, lifetime access, doubt support, and 6 individual course certificates, you’ll gain practical knowledge to safeguard systems, spot vulnerabilities, and launch a career in cybersecurity — all without needing prior coding experience. It’s the perfect way to build a secure, future-ready skill set in a world that’s more connected—and vulnerable—than ever.
Got Questions?
Check Out Our FAQs!
This bundle is designed for students, working professionals, beginners, and tech enthusiasts who want to understand and work in the field of cybersecurity. No prior coding experience is required.
You’ll learn key cybersecurity domains including Ethical Hacking, Network Security & Defense, Mobile Hacking Techniques, Dark Web Intelligence, Cyber Forensics, and Advanced Penetration Testing. Each course focuses on hands-on tools and real-world use cases.
Yes! You will receive 6 individual certificates, one for each course you complete in the bundle. These certificates can be added to your LinkedIn profile, resume, or shared with employers to showcase your skills.
You get lifetime access to all the courses included in this bundle. You can revisit and learn at your own pace, anytime.
Yes. We offer a 7-day refund policy from the date of purchase if you’re not satisfied with the course.
You’ll work with popular cybersecurity tools like Kali Linux, Burp Suite, Wireshark, Metasploit, Nmap, and many more…All tools used are free or open-source, and we guide you step-by-step in setting them up.
Yes, you’ll have access to dedicated doubt support and community forums where you can get help from mentors and fellow learners.
Not at all! This course is beginner-friendly and explains everything from the ground up — no technical background required.
Don’t Miss This Special Offer – 80% OFF on Cybersecurity Combo Bundle!
Limited Period Offer
Don’t Miss This Special Offer – 80% OFF on Cybersecurity Combo Bundle!
Limited Period Offer
Maltego - Discovering Websites Hosting Provider Emails
What are they And How To Discover Exploit Basic File Upload Vulnerabilities
HTTP Requests - GET - POST
Intercepting HTTP Requests
Exploiting Advanced File Upload Vulnerabilities
Exploiting More Advanced File Upload Vulnerabilities
Security Fixing File Upload Vulnerabilities
What are they How To Discover Exploit Basic Code Execution Vulnerabilities
Exploiting Advanced Code Execution Vulnerabilities
Security - Fixing Code Execution Vulnerabilities
What is SQL?
Dangers of SQL Injections
Discovering SQL Injections In POST
Bypassing Logins Using SQL Injection Vulnerability
Bypassing More Secure Logins Using SQL Injections
Security Preventing SQL Injections In Login Pages
Discovering Exploiting Blind SQL Injections
Discovering SQL Injections And Extracting Data Using SQLmap
Getting a Direct SQL Shell using SQLmap
Introduction - What is XSS or Cross Site Scripting
Discovering Basic Reflected XSS
Discovering Advanced Reflected XSS
Discovering An Even More Advanced Reflected XSS
Discovering Stored XSS
Discovering Advanced Stored XSS
Hooking Victims To BeEF Using Stored XSS
Hooking Targets With Beef
Capturing ScreenShot Of Target
Redirecting Target To Any Website
Force Target To Watch Youtube Video
Steal FacebookGmail Password Using Beef